A successful data breach response plan delivers rapid, coordinated action when a security incident threatens your organization’s data and reputation. This guide outlines the purpose, structure, and practical steps you need to build a resilient response framework—from preparation to recovery and continuous refinement. By following these proven strategies, business leaders can minimize downtime, control costs, and maintain stakeholder trust.
Key Elements Of A Data Breach Response Plan
When chaos strikes, a written guide removes hesitation and clarifies each team’s role.
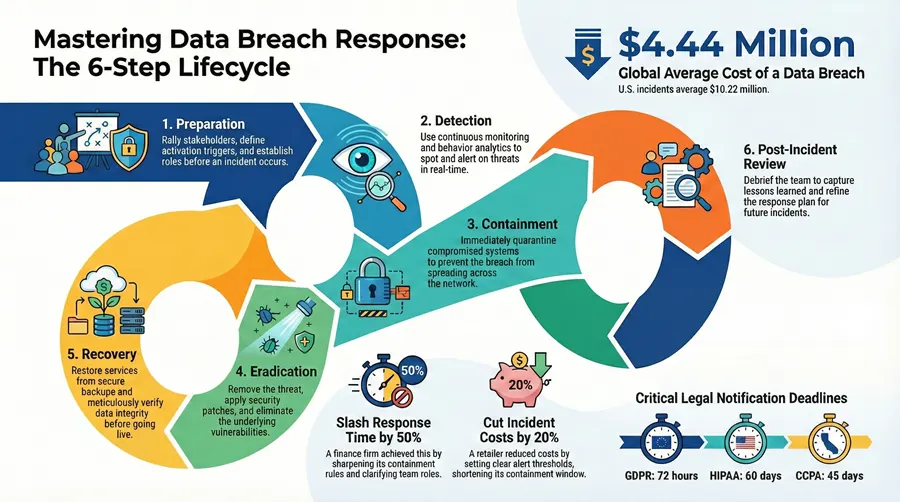
- Preparation: Rally stakeholders, define activation triggers, update contact chains.
- Detection: Deploy continuous monitoring to spot odd behavior as it happens.
- Containment: Quarantine compromised systems so the breach can’t spread.
- Eradication: Remove threats, apply patches, and lock down vulnerabilities.
- Recovery: Restore from backups, verify data integrity, then bring services back online.
- Post-Incident Review: Debrief the team, capture insights, and refine procedures.
Core Phase Connections
In one mid-sized finance firm, sharpening containment rules slashed response time by 50%.
This diagram shows how early preparation feeds into faster detection, driving rapid isolation and control. Assigning precise roles—backed by measurable benchmarks—keeps IT, legal, and communications teams aligned under pressure.
Read also our guide on backup and recovery strategy plan for detailed support strategies that map to recovery objectives.
Structure and accountability are essential for reducing breach impact and accelerating system recovery.
Accountability Drives Success
Flagging responsibilities upfront means nobody has to guess the next move. Metrics such as time to detection or first-pass recovery rate become your scoreboard. One retailer went from a four-hour containment window to under two hours after setting clear alert thresholds, cutting incident costs by 20%.
Measuring Success
- Time to Detection: Speed from breach trigger to alert.
- Containment Duration: How long systems stay isolated.
- Recovery Point Objectives: Maximum acceptable data loss.
- Post-Incident Review Scores: Team performance and task completion rates.
Tracking these metrics keeps your data breach response plan nimble and ever-improving.
Continuous Updates
Regular tabletop exercises and plan walkthroughs ensure you’re never caught off guard as threats evolve.
Building Your Response Team And Resources
A breach response demands people, processes, and budgets aligned before alerts fire. Begin by mapping existing skills across IT, legal, and communications teams and assigning each role to a critical function.
- Security Analysts – Scan logs and spot anomalies in real time.
- Legal Counsel – Advise on breach notification laws and filing requirements.
- Public Relations Specialist – Shape stakeholder updates and press releases.
- IT Operations Lead – Orchestrate system shutdowns, patching, and restorations.
In smaller outfits, roles often overlap. Cross-train two or three members on each task to boost initial response speed. At a Seattle-based startup, rotating an on-call responder cut first-response time by 35% in three months.
For complex incidents, pre-engage external partners. A digital forensics firm can secure volatile data, while a regulatory consultant helps navigate cross-border notification rules.
Identifying Core Incident Roles
Define authority, investigation ownership, and executive updates before a breach hits.
- Incident Manager – Triggers the plan and rounds up the response squad.
- Lead Investigator – Digs into logs, preserves evidence, charts attack paths.
- Communications Lead – Crafts and signs off on public statements.
- Compliance Officer – Verifies notifications hit every legal deadline.
“Clarity in roles cut response time by 40% at a regional healthcare provider,” recalls CISO Jane Thompson.
Allocating Tools And Budget
Prioritize the tools and services you’ll need, then assign budget ranges.
- SIEM Platforms – Real-time log gathering and alerts
- Forensic Services Retainer – Fast-track investigation
- Crisis Communications Platform – Secure messaging, media monitoring
- Encrypted Channels – Shield internal updates
- On-Demand Breach Coaching – Expert guidance when you need it
Keep a live inventory of servers, applications, and vendor SLAs in a central dashboard. Include third-party vendors in your contact matrix to avoid surprise downtime.
| Resource Type | In-House Advantages | When To Bring In External |
|---|---|---|
| Security Analysts | Immediate response, cost-efficient | Complex malware or zero-days |
| Legal Counsel | Deep corporate insight | Cross-border compliance |
| PR Specialists | Knows your voice | High-profile or public cases |
| Digital Forensics | N/A | Evidence preservation |
Establishing Communication Channels
- A dedicated, encrypted Slack channel for rapid collaboration
- A phone tree with 24/7 on-call rotation
- A secure document repository for incident artifacts
- Automated SMS alerts for critical escalations
“A reliable alerting system reduces time to containment by 25%,” notes cybersecurity veteran Marcus Lee.
Schedule regular drills to test both technology and workflows. Document the escalation matrix in your data breach response plan for quick reference.
You might be interested in learning how managed security services enhance team readiness in our article managed security services benefits.
Detecting And Containing Breaches Quickly
Every second counts when a breach hits. Your playbook should combine real-time log aggregation, user behavior analytics, and curated threat intelligence.
- Log Monitoring centralizes system events for streamlined review.
- User Behavior Analytics flags outliers in login and data-access patterns.
- AI-Driven Anomaly Alerts highlight deviations from normal operations.
- Threat Intelligence Feeds bring context on emerging attack vectors.
Proven Detection Techniques
Tuning smart thresholds cuts alert noise. For example, raising the bar on failed login attempts can drive down false positives by 40%. Regular drills and refined incident criteria help organizations contain breaches 30% faster.
According to Varonis, the global average cost of a breach is $4.44 million, while U.S. incidents average $10.22 million.
Average Data Breach Costs by Region And Sector
| Category | Average Cost |
|---|---|
| Global Average | $4.44 million |
| United States | $10.22 million |
| Healthcare Sector | $9.23 million |
| Mega Breaches | $401 million |
Immediate Quarantine Procedures
- Pinpoint the host or subnet exhibiting malicious behavior.
- Sever external and lateral network links to halt spread.
- Rotate credentials and lock down compromised accounts.
- Spin up isolated environments for forensic deep dives.
- Roll out patches or configuration tweaks to shut out attackers.
Rapid isolation buys time to analyze threats and keeps critical assets safe.
Coordinating Investigations
Containment and investigation should run side by side. Appoint an internal incident lead while a digital forensics partner maps the attacker’s trail. Clear, concise updates to executives and regulators make decision-making smoother.
Clear communication channels stop confusion and align teams under pressure.
Engaging External Partners
Preselect:
- Digital forensics firms that preserve evidence and map attacker tactics.
- Managed detection and response (MDR) services for around-the-clock monitoring.
- Legal advisors versed in multi-jurisdictional breach notification laws.
Fast Executive Notification
Provide leadership with a concise dashboard: scope, impacted systems, containment progress, and key metrics. Automated status updates eliminate constant check-ins and keep everyone aligned.
Tuning Alert Accuracy
Review your SIEM and analytics configurations quarterly:
- Adjust thresholds to mirror real incident patterns.
- Retire outdated rules that trigger on harmless behavior.
- Work with threat feed providers to fine-tune IoC and TTP data.
A regional logistics firm trimmed false positives by 60% simply by refining file-integrity monitoring rules.
Maintaining Quick Response
Link detection, containment, and collaboration to cement resilience. Ongoing threshold tweaks, realistic drills, and clear partner roles keep your plan agile and cost-effective.
Practicing full-scale exercises with your response team speeds up containment by up to 30%.
Contact 1-800 Office Solutions now to sharpen your data breach response plan and claim your complimentary readiness assessment.
Recovering Systems And Data Securely
When you control the breach, focus shifts to restoring systems and data with confidence.
- Backup Verification: Run checksum tools to confirm file integrity.
- Rollback Procedures: Test restores in a sandbox before production.
- Incremental Restoration: Bring services back in stages, watching logs for anomalies.
A regional law firm validated 100% of critical files, cutting downtime from eight hours to two.
Validate Data Integrity
- Generate and record checksums before restoration.
- Compare live data against snapshots.
- Flag and resolve any discrepancies.
“Data verification cut our restore errors by 75% and boosted confidence in every recovery.”
Rebuilding Applications
- Isolated Build Servers: Air-gapped environments.
- Configuration Management: Secure baselines under version control.
- Staged Rollouts: Update a subset first, then expand.
A SaaS provider caught a configuration flaw early, shaving 30% off total restore time.
Conduct Forensic Analysis
Dive into our guide on Computer Forensic Analysis Best Practices for techniques.
- Preserve volatile memory before reboot.
- Capture network logs, disk images, and malware samples.
- Time-stamp every action for an accurate timeline.
Legal And Customer Communications
Under GDPR you have 72 hours; missing it can cost €20 million or 4% of global revenue.
- Notification Letters: Customizable templates for regulators and affected parties.
- Media Statements: Press release drafts that convey control.
- Internal Alerts: Scripts for employee briefings.
One software firm notified customers quickly, offered complimentary credit monitoring, and saw trust scores climb by 25%.
| Regulation | Notification Deadline |
|---|---|
| GDPR | 72 hours |
| CCPA | 45 days |
| HIPAA | 60 days |
After systems are live, schedule a post-incident review. Document what worked, what didn’t, and update your playbooks. Ready to tighten up your recovery workflows? Contact our experts at 1-800 Office Solutions for a personalized review.
Enhancing Your Response Plan After An Incident
Post-incident reviews reveal real improvements. Swap vague notes for a structured after-action report and feed learnings directly into your next data breach response plan update.
Key Metrics For Post Incident Review
- Time to Detection Improvement
- Mean Time to Resolution (MTTR)
- Playbook Coverage Rate
- Tabletop Exercise Success Scores
- Contact List Accuracy
Templates For After Action Reports
- Executive Summary
- Chronological Timeline
- Root Cause Analysis
- Action Items
- Lessons Learned
Refining Your Playbooks And Escalation Paths
- Refresh contact lists quarterly.
- Define clear thresholds for each severity level.
- Add secondary contacts.
When playbooks go stale, every lost second counts toward bigger losses.
Integrating Lessons Into Tabletop Exercises
- Craft scenarios from past incidents.
- Assign actual team members to roles.
- Score responses against playbook metrics.
- Debrief immediately and schedule the next drill.
Updating Communication Templates
- Verify legal disclaimers.
- Refresh customer FAQs.
- Polish social-media posts.
Aligning Legal And Compliance Reviews
- Revisit threshold definitions.
- Confirm log retention for audits.
- Check vendor contracts for notification duties.
Stay on track with 1-800 Office Solutions for help scheduling or running reviews.
Actionable Templates And Checklists For Your Plan
Equip your team with ready-to-use templates that slot into any data breach response plan.
- Incident Escalation Checklist
- Breach Notification Letter Template
- Communications Plan Outline
- Compliance Tracking Matrix
Incident Escalation Checklist
- Detection triggers with timestamps
- Containment actions tied to system IDs
- Communication steps paired with approved templates
- Escalation contacts and fallback options
Breach Notification Letter Template
- Date and time of discovery
- Nature and scope of breach
- Data categories exposed
- Notification recipients and timeline
Communications Plan Outline
- Internal briefings with IT, legal, and PR
- Customer and partner advisories
- Media statements
- Social media alerts
Compliance Tracking Matrix
| Task | Owner | Deadline | Status |
|---|---|---|---|
| Incident Escalation | Team Lead | Within 1 hour | In Progress |
| Notification Submission | Compliance | 72 hours | Pending |
| External Communication Setup | PR Lead | 4 hours | Done |
Using Templates In Drills And Incidents
- Include templates in quarterly sessions.
- Update fields on the fly during activations.
- Review completed checklists for audit trails.
- Rotate owners to validate backup contacts.
Tips For Effective Customization
- Validate legal clauses with counsel.
- Add regional regulation details.
- Prepopulate backup contacts.
- Align deadlines with internal policies.
Continuous Improvement And Audit Readiness
- Run audit walkthroughs every six months.
- Archive completed checklists for two years.
- Track revision history.
- Collect reviewer sign-offs.
Practice makes perfect. Run focused exercises every six months and full-scale simulations once a year.
- Tabletop Exercises reveal gaps in internal communication.
- Red Team Simulations test detection and containment.
- Recovery Drills restore systems under tight deadlines.
Notification Requirements
| Jurisdiction | Deadline |
|---|---|
| GDPR | 72 hours |
| CCPA | 45 days |
| HIPAA | 60 days |
Miss your deadlines and you risk steep penalties. To keep costs in check:
- Set aside 2–5% of your annual IT budget for plan upkeep.
- Use open-source monitoring tools when possible.
- Engage pay-as-you-go forensic experts for deep dives.
AI Tools And Oversight
AI accelerates detection—but false positives can overwhelm you. Balance precision thresholds with human checkpoints.
“Effective AI alerting balanced with human oversight reduced our false positives by 60%,” says security architect Maria Chen.
- Require an analyst review each AI flag within 15 minutes.
- Track false positives monthly and refine models.
Conclusion
A well-designed data breach response plan empowers your organization to prepare, detect, contain, and recover with confidence. By following these essential steps—backed by real-world examples and measurable benchmarks—you’ll minimize downtime, control financial risk, and maintain stakeholder trust. Continuous improvement through drills, reviews, and updated playbooks ensures you stay one step ahead of evolving threats.
Ready to strengthen your response framework? Contact 1-800 Office Solutions today for expert guidance, comprehensive assessments, and tailored solutions. Schedule your complimentary readiness review and fortify your defenses now.
Visit 1-800 Office Solutions to download your free toolkit. No signup required.