Automation and Integration: Automation Is Becoming Crucial for Managing Vast Amounts of Data Securely
AI Overview:
This blog explains how automation and integration work together to secure, manage, and optimize data in modern organizations. It highlights how technologies like APIs, iPaaS, RPA, and integration platforms streamline data collection, storage, and processing while reducing human error and improving efficiency. The article also covers key benefits—such as stronger data security, cost savings, and scalability—alongside challenges like legacy system integration, access control, and implementation costs. Overall, it presents automation and integration as essential pillars of a secure, efficient, and future-ready data strategy.
Automation and Integration
The modern world is increasingly reliant on data for both personal and professional use. As this reliance continues to grow, so too does the need for secure data management. Automation and integration is quickly becoming an essential part of this quest for security. To facilitate the secure storage and management of vast amounts of data, automation is needed to ensure the right processes are followed.
The automation of processes can help to streamline the data management process, allowing for a secure environment that is free from human error. It can help to identify and flag any issues quickly, as well as allowing for a more efficient way to tackle any problems that arise. Automation and integration can also help to ensure that data is properly secured and protected, allowing users to have peace of mind that their data is safe from any malicious actors.
Introduction to Automation and Integration
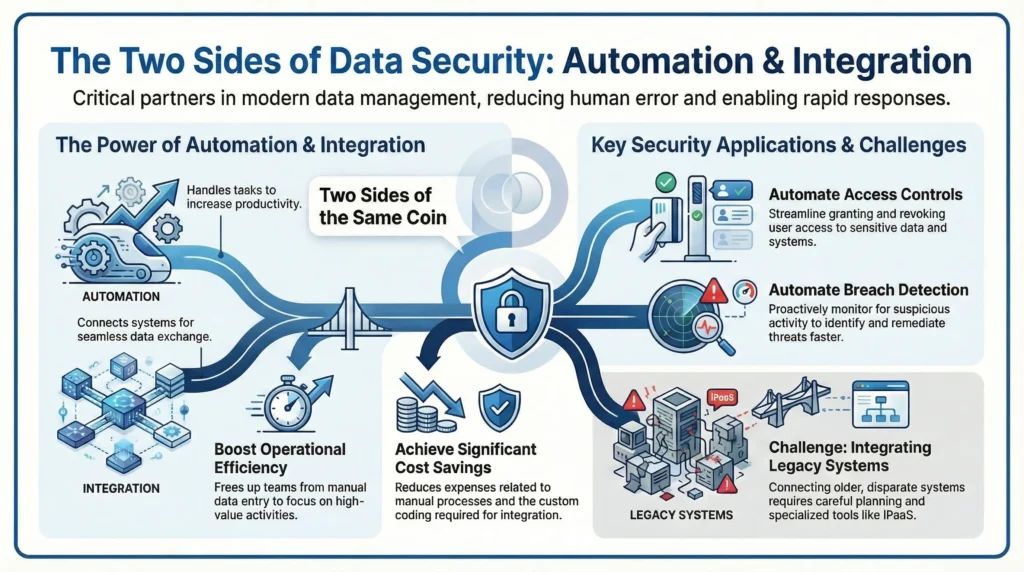
As a Chief Data Security Officer, it is essential to understand the significance of automation and integration, and the benefits and challenges associated with it. Automation and integration are two sides of the same coin. Automation refers to the process of automating tasks using technology, while integration is the process of connecting various applications, software, and systems.
Using different tools and techniques, organizations can automate processes, workflow, and business operations. APIs, integration platforms, and interface connectors are used to establish a connection between different software applications.

Defining Automation and Integration
As a Chief Data Security Officer, I understand the importance of automation and integration in today’s digital landscape. Automation and integration are two sides of the same coin and involve connecting different software applications, systems, and users, to create efficient business processes. Automation is the process of automating the workflows and processes to reduce manual effort and increase productivity. Integration is the process of connecting different systems and applications to enable data transfer and exchange of information from one system to another.
At the core of automation and integration lies the concept of application programming interfaces (APIs), which are used to connect different applications and systems. APIs allow organizations to integrate data from one system to another, and automate business processes across different systems. Companies can leverage Integration Platform as a Service (iPaaS) solutions, Robotic Process Automation (RPA), Enterprise Service Bus (ESB) solutions, and pre-built integration templates to automate and integrate their business operations.
Integration and automation tools like MuleSoft and Jitterbit provide organizations with the ability to connect different software applications, synchronize data across different systems, and automate processes. By automating and integrating business operations, organizations can streamline their processes, improve customer experience, and gain a competitive edge.
Benefits of Automation and Integration
As businesses continue to evolve, so too must the tools they use to stay competitive. Enter automation and integration: the two sides of the same coin that provide organizations with a distinct advantage over their competition. Automation and integration, when implemented properly, can help to streamline business operations, improve user experience, and create a single source of truth for all organizational data.
The benefits of automation and integration are numerous and varied. Here are just a few examples of how businesses can benefit from this approach:
- Improved Efficiency: Automating processes and integrating disparate systems can help to free up time and resources, allowing business users to focus on more value-added activities. This may include integrating ERP and CRM systems, or connecting different software applications with an integration platform.
- Enhanced User Experience: By using pre-built integration templates, businesses can create seamless user experiences across different systems, increasing customer satisfaction.
- Cost Savings: Automating and integrating systems can help to reduce costs associated with manual data entry, as well as the cost of coding required for integration.
- Competitive Edge: Automation and integration can give businesses a competitive edge by increasing the speed and accuracy of order fulfillment, as well as providing APIs for customers to use.
Challenges of Implementing Automation and Integration
Having discussed the benefits of automation and integration, it is also important to consider the challenges associated with implementing such a system. Many organizations often experience difficulty when trying to generate a unified approach to automation and integration. The complexity of such a task lies in the need to connect different applications, software, and systems across different platforms, while also ensuring data security and compliance. Furthermore, the task of mapping and transforming data from one system to another can become a bottleneck, especially when coding is required.
Organizations must also consider the coordination and alignment of different tools like email marketing, ERP, CRM, and automation vendors in order to achieve their business goals. Additionally, the advantage of integration is only realized when companies can successfully automate processes and integrate systems across different business operations.
This requires an automation approach that is scalable, secure, and delivers a good user experience. Without such an approach, organizations are left with siloed data, where the value of each piece of data is diminished.
The use of pre-built integration templates, cloud services, and integration platforms like iPaaS, RPA, and ETL can help streamline the automation and integration process.
Automation and Data Management
Data automation and integration have become increasingly important in today’s digital landscape. Automation tools and integration platforms provide a powerful way to connect different software applications and automate processes to improve efficiency, streamline workflows, and enable users to take advantage of the benefits of automation and integration.
APIs (Application Programming Interfaces) also provide a way to integrate systems, transfer data from one system to another, and connect different cloud services. Robotic Process Automation (RPA) and Integration Platforms as a Service (iPaaS) are popular tools used to automate and integrate complex business processes.
Automation for Data Collection
The benefits of automation and integration become increasingly important in today’s digital landscape. Automation for data collection is a critical part of the process to streamline business operations and become more efficient. By automating and integrating different applications across different systems, organizations can free up time to focus on more important tasks while also providing better service to customers.
Integration and automation tools like application programming interfaces (APIs), enterprise service bus (ESB), and integration platform as a service (iPaaS) connect different software applications and systems to enable users to move data from one system to another. This process eliminates the need for coding and manual data transfer. Pre-built integration templates, connectors, and workflow tools allow organizations to quickly and easily map and transform data across different systems.
Robotic process automation (RPA) and marketing automation tools can also become a part of the data collection process. By automating tedious processes and tasks using RPA, users can improve efficiency and accuracy, while marketing automation helps to create a better customer experience. These tools often come with user-friendly interfaces and require minimal change management.
Automation for Data Storage
With the introduction of automation and integration, comes the need for secure and efficient data storage and management. As the Chief Data Security Officer for a company, it is imperative to understand the automation for data storage and the various solutions available in the market. Automation for data storage applies the principles of automation to the storage and management of data, allowing for a secure, streamlined, and efficient process.
Various automation tools are available to manage and store data, depending on the company’s needs. Many of these tools are designed to automate the collection, processing, and storage of data. This includes integration and automation platforms, enterprise service buses, and integration solutions that connect different software applications. With these solutions, companies can streamline their data storage process and gain a competitive edge in the digital landscape.
Popular tools like APIs, RPA, and iPaaS are enabling companies to automate and integrate their data storage processes. APIs also provide a way to connect different software applications, allowing for a single source of truth for data. Additionally, pre-built integration templates, connectors, and orchestration tools are available to automate the integration process, eliminating the need for coding and manual data entry.
Automation for Data Processing
With the goal of making data processing more efficient and flexible, integrating automation into the data processing workflow has become increasingly important in today’s digital landscape. Automation for data processing enables business users to automate processes, free up time, and improve efficiency in order to meet their business goals. By connecting different software applications, companies can automate and integrate different tools like ERP, CRM, marketing automation, order fulfillment systems, and more.
Application programming interfaces (APIs) provide a powerful way to connect different systems in an organization and transfer data from one system to another. This is done through mapping and transformation of data across multiple systems. End-to-end automation and integration of data can be achieved through an Integration Platform-as-a-Service (iPaaS) solution, providing pre-built integration templates to streamline the automation process and reduce the coding required.
Robotic process automation (RPA) is another tool used to automate the integration process and provide a single source of truth across different applications. Companies can use a combination of RPA and iPaaS solutions to coordinate and align their business operations with their digital transformation goals. This synchronizes the data from multiple systems, allowing for a seamless user experience.
Benefits of Automation and Integration
Integration and automation are two sides of the same coin – when done correctly, they can enable businesses to receive the maximum benefits of automation and integration. Automation and integration can help improve data security, increase efficiency, and save costs. With automation, businesses can streamline their processes and drive greater efficiency.
Automation tools like RPA, ETL, and iPaaS provide businesses with powerful automation solutions they can use to reduce the time and effort involved in manual data entry and other manual processes. Furthermore, automation helps to ensure data accuracy and reduce the likelihood of human error.
Improved Data Security
The benefits of automation and integration are clear, however, one of the greatest advantages of this approach is improved data security. Automation and integration can effectively reduce the risk of data breaches due to human error, malicious actors, or simply outdated technology. By using an automated and integrated approach, organizations can be sure that their data is secure and free from potential threats.
In order to ensure that data is secure, organizations should consider the following:
- Implementing Secure Processes and Practices: Organizations should ensure that their processes and practices are secure and up-to-date. This includes using automated processes, such as workflow automation, to prevent unauthorized access to data. Additionally, organizations should consider using an integration platform to allow for secure connections between different systems.
- Using Automation Tools: Automation tools, such as robotic process automation (RPA), can be used to automate tedious and complex processes. By automating these processes, organizations can ensure that their data is secure and protected from potential threats. Additionally, automation tools can be used to connect different systems in order to ensure that data is secure and up-to-date.
Increased Efficiency
The increased efficiency that automation and integration bring to a business can be profound. Companies that have made the switch to a streamlined, automated approach to their business processes are reaping the rewards. Data can now move between different systems quickly and accurately, with little to no manual effort required.
With end-to-end integration and automated workflows, organizations can synchronize data between different applications, eliminating siloed data and manual data entry. By connecting different software applications, businesses can automate processes, such as order fulfillment, to reduce manual effort and improve customer experience. Process automation and integration can also free up time for employees to focus on more value-added tasks.
Organizations can also leverage the benefits of automation and integration to streamline their business operations and take advantage of a competitive edge. Automation and integration solutions, such as application programming interfaces (APIs) and enterprise service buses (ESBs) allow businesses to transfer data from one system to another, creating a single source of truth.
Connectors and pre-built integration templates can make it easier to integrate different tools and cloud services, while orchestration tools and robotic process automation (RPA) can help to automate the integration process. By automating and integrating different tools, businesses can eliminate manual work, reduce bottlenecks, and improve business goals.
Cost Savings
The cost savings that can be achieved through automation and integration are often overlooked. By streamlining processes and eliminating manual tasks, organizations can reduce their labor costs and become more efficient. Additionally, organizations can become more competitive by leveraging pre-built integration templates and API connections to sync data and applications across different systems.
Automation and integration can also provide a competitive edge by enabling users to coordinate and align business operations with their business goals. Gartner Analyst predicts that organizations that automate and integrate their processes and data will be able to reduce costs, improve customer experience, and gain a greater advantage over their competitors.
Automation and integration can minimize the need for manual data entry, reduce the time and effort required to transfer data from one system to another, and free up time for more valuable tasks. Automating the integration process can also reduce the amount of coding required, reducing the need for developers and further cutting down on labor costs. Automation and integration tools can also help organizations save money by eliminating manual tasks like order fulfillment and customer service.
Businesses can also save money by leveraging integration and automation platforms, such as MuleSoft and Jitterbit, to connect different software applications, eliminating the need for custom coding and free up valuable resources.
Integrating Automation with Security
Integrating automation with security has become increasingly important in today’s digital landscape. Automating access controls, automating data encryption, and automating breach detection are all sides of the same coin. Automation tools such as Robotic Process Automation (RPA) and Enterprise Service Bus (ESB) enable users to streamline business processes, connect different software applications, and automate processes to improve efficiency.
Integration Platform as a Service (iPaaS), APIs, and workflow orchestration tools provide users with pre-built integration templates to connect different systems, sync data, and automate and integrate complex business processes.
Automating Access Controls
The combination of automation and integration can provide an effective solution for securing data. Automating access controls is a key component of this strategy, as it allows organizations to regulate who is able to access which systems and data. It requires weaving together a complex set of procedures that ensures that access is distributed in a way that is consistent with the organization’s policies and goals.
To facilitate this, organizations can leverage integration and automation tools like Robotic Process Automation (RPA) and Enterprise Service Bus (ESB) to connect different applications and quickly automate processes. This can streamline the process of granting and revoking access while also providing an audit trail. By integrating and automating access controls, organizations can minimize the risk of those with malicious intent gaining access to valuable data.
Using an integration platform as a service (iPaaS) can also be beneficial in automating access controls. It provides a visual workflow for mapping and transformation of data between the different systems, while also giving the organization the ability to connect different tools like CRM, ERP, and marketing automation. It can also provide pre-built integration templates to quickly sync data across different software applications.
Ultimately, automating access controls is a crucial step in improving the security of an organization’s data.
Automating Data Encryption
The security of a business is paramount and, when combined with automation and integration, the result is a powerhouse of protection. Automating data encryption is a key part of this process, and is a powerful way to secure information and ensure that only those with permission can access it.
Data encryption, put simply, is the process of scrambling plain text into an unreadable format. This scrambling process is then reversed to turn the unreadable data back into plain text with the use of a decryption key. The encryption algorithm used is the most important factor to take into account when automating data encryption. This algorithm is the mathematical formula used to convert the plain text into the scrambled format.
The advantage of automating data encryption is that it eliminates human error and is much faster than manual encryption. The process is also repeatable and scalable, making it possible to encrypt large amounts of data quickly and easily. Additionally, automation can be used to ensure that all data is encrypted, as manual processes can often miss certain areas.
Another important factor to consider when automating data encryption is the decryption key. This key is used to reverse the encryption process, and needs to be stored securely and only made available to those with permission.
Automating Breach Detection
In the modern digital landscape, automating breach detection is becoming increasingly important in today’s organizations. Robotic Process Automation (RPA), Application Programming Interfaces (APIs), and Integration Platform as a Service (iPaaS) are just some of the tools used to automate and detect potential breaches. Each of these tools can be used to securely integrate systems and streamline the process of detecting breaches.
To ensure the success of automating breach detection, organizations often need to:
- Leverage pre-built integration templates: Pre-built integration templates provide an efficient way to quickly sync data across different systems. By leveraging pre-built integration templates, organizations can quickly detect any suspicious activity.
- Use Orchestration Tools: Orchestration tools like MuleSoft and Jitterbit can be used to coordinate and align activities of different software applications. These tools can enable users to automate processes and improve efficiency when it comes to detecting and responding to breaches.
- Provide APIs: Providing APIs to different tools can enable organizations to quickly detect breaches. APIs also allow organizations to connect different applications and transfer data from one system to another.
By leveraging the right automation and integration tools, organizations can quickly detect any suspicious activity that could lead to a breach.
Challenges of Automation and Integration
Integrating with legacy systems, managing access and permissions, and the cost of implementation are all integral elements of the process of automation and integration. Without proper integration, automation can be a difficult process, with manual effort required to sync different systems.
API management and end-to-end integration are necessary for complete automation, while ensuring a seamless user experience. Business applications, such as CRM, ERP, and order fulfillment systems, must be integrated to maximize the benefit of automation. With the right tools and a well-planned approach, organizations often find that the advantages of automation and integration far outweigh the costs.
Cost of Implementation
Having established the importance of automation and integration, the next step is to consider the cost of implementation. While the long-term benefits of automation and integration are widely recognized, organizations must first address the upfront cost of introducing automation into their business processes. The cost of integration can be broken down into two main categories: technology-related expenses and personnel-related expenses.
The technology-related expenses include the cost of purchasing, configuring, and customizing the automation and integration tools, as well as the cost of any APIs and connectors that may be necessary. Additionally, organizations may need to invest in additional software applications and cloud services to facilitate the integration process, or they may choose to purchase an existing integration platform such as an Enterprise Service Bus (ESB) or Integration Platform as a Service (iPaaS).
Organizations must also consider the cost of personnel-related expenses, such as training employees on the new automation and integration tools, and hiring additional personnel to manage the automation processes. Additionally, organizations may need to invest in change management to ensure that employees are adequately prepared for the transition and that the automation and integration processes are aligned with the organization’s business goals.
Organizations should also consider the long-term costs associated with maintaining and troubleshooting the automation and integration processes.
Integrating with Legacy Systems
Transitioning from the previous section, the topic of integrating automation with security leads to the challenges of automation and integration, particularly when it comes to legacy systems. While the benefits of automation and integration are clear, the cost of implementation can be prohibitive for some organizations. Integrating with legacy systems presents a unique set of challenges. As such, organizations must be mindful of the potential issues that may arise from integrating disparate systems, such as the need to manage access and permissions.
In order to successfully integrate automation and legacy systems, organizations must carefully consider their existing infrastructure and the ways it might need to be adapted to accommodate the new technology. This could include implementing an integration platform, such as an enterprise service bus or application programming interface (API) management solution, to connect the necessary systems. Additionally, organizations should consider the use of pre-built integration templates and tools to automate and streamline the integration process.
The digital landscape continues to evolve, and organizations must be agile enough to keep up with the changes. To ensure the success of automation and integration, organizations must be able to connect different systems and applications across the enterprise, while still allowing for the necessary levels of security. Automating the integration process is one of the most effective ways to ensure that data is accurately and securely transferred from one system to another.
Managing Access and Permissions
As automation and integration become increasingly important in today’s digital landscape, managing access and permissions become integral in creating a secure and automated system. Achieving secure automation requires organizations to carefully evaluate the user experience, the integration and automation tools available, and the access and permissions granted to ensure that no unauthorized data is shared or accessed.
Organizations often need to connect different software applications and systems to automate processes and improve efficiency. To do this, they need to coordinate and align different tools like application programming interfaces (APIs), enterprise service buses (ESBs), and robotic process automation (RPA) to connect different systems. This will enable users to transfer data from one system to another and provide a single source of truth.
Tools such as Integration Platform as a Service (iPaaS) and pre-built integration templates can help streamline the automation and integration process by eliminating the coding required to sync data across different applications like customer relationship management (CRM), enterprise resource planning (ERP), and order fulfillment systems. Benefits of automation and integration include freeing up time for business users to focus on more business-related tasks and providing better service to customers.
Automation Best Practices
Setting up automation rules is key for successful automation best practices. Automation and integration become increasingly important in today’s digital landscape, allowing organizations to gain a competitive edge and improve efficiency. Automation tools, such as robotic process automation (RPA), enterprise service bus (ESB), application programming interfaces (APIs), and integration platforms (iPaaS), provide a single source of truth and enable users to connect different software applications. Process automation and integration solutions provide APIs to streamline the user experience, create automated workflows, and sync data across multiple systems.
Setting up Automation Rules
The transition to setting up automation rules is a natural one. Automation and Integration processes, while two sides of the same coin, become increasingly important in today’s digital landscape. Automation and integration tools like Integration Platform as a Service (iPaaS), Robotic Process Automation (RPA), Extract, Transform and Load (ETL) tools, and API Management tools have become essential for businesses to achieve a competitive edge.
Organizations often find themselves trying to integrate siloed software applications, automate processes in order to improve efficiency, and connect different applications in order to provide a better user experience. Setting up automation rules is the first step in achieving these goals. Here are some tips on how to get started:
- Understand Your Business Goals: Automation is a powerful tool to streamline business operations, but it requires a clear understanding of the desired outcome. Automation should be used to enable users to do their jobs more efficiently. It is important to consider the organization’s goals and how automation can help achieve them.
- Choose the Right Tools: With the wide array of automation and integration tools in the market, it is important to evaluate the different vendors and choose the one that best fits the organization’s needs.
Regularly Auditing Automation Processes
Having laid out the challenges of automation and integration, it is now necessary to develop best practices for setting up, auditing, and monitoring automation processes. Regularly auditing automation processes is of paramount importance, as it is the only way to ensure that all automation processes are running smoothly and securely. As a Chief Data Security Officer, a fundamental part of my job is to thoroughly audit all automation processes.
Auditing automation processes involves evaluating the automation workflows that have been set up, as well as the tools and applications that are used. This includes evaluating the data integration solutions, application programming interfaces (APIs), connectors, and other tools that are used in the automation process.
Furthermore, it is important to review the different software applications and systems that are being integrated, as well as any customer experience or marketing automation processes that are being implemented. It is also necessary to ensure that the process integration is configured correctly and that the automation approach is efficient and scalable.
In addition, auditing automation processes should involve the review of any user experience that is being impacted by the automation. This includes identifying any bottlenecks that may arise due to automation, such as coding requirements or data transfer issues.
Monitoring Automation Performance
Having a successful automation and integration strategy requires regular, ongoing monitoring to ensure that the process is up to date and functioning as intended. When it comes to monitoring automation performance, organizations must take a few steps in order to ensure that their optimized processes are running smoothly. This includes setting up automation rules, regularly auditing automation processes, and monitoring automation performance.
The first step in monitoring automation performance is to establish rules for automating processes. These rules should govern the particulars of the automation process, such as who is responsible for initiating the automated workflow and when and how it should be triggered. Additionally, organizations should use automation tools to keep track of the different data points and metrics associated with the process, as well as the progress of the automation process itself.
Organizations should also audit their automation processes on a regular basis. This involves reviewing the progress of the automation process, validating the accuracy of the data being used, and making sure that the automation process is following best practices. Auditing the automation process also allows organizations to identify any potential bottlenecks or issues that could impede its progress, as well as any opportunities to optimize the process for improved efficiency.
Finally, organizations should continuously monitor their automation performance and make any necessary adjustments.
Integration Best Practices
To ensure successful Integration Best Practices, it is vital to establish a data strategy, identify relevant data sources, and build a robust integration system. Automation and Integration are two sides of the same coin; they both work together to streamline business processes and improve efficiency. Automation tools become increasingly important in today’s digital landscape, as they enable users to automate and integrate processes across different software applications.
Organizations often turn to integration platforms, such as iPaaS, to connect different systems and applications. This allows them to integrate and automate data transfer between their CRM, ERP, and other software tools.
Establishing a Data Strategy
In order to build a resilient and effective integration system, organizations must first establish a comprehensive data strategy. A data strategy will define the parameters for how data is collected, stored, managed, and shared across an organization. This strategy should include an assessment of the current data landscape, an identification of the data resources needed to achieve the organization’s business objectives, and an implementation plan for integrating those resources.
To build a successful data strategy, organizations should first identify the relevant data sources that will help meet their goals. This includes both internal and external sources such as customer relationship management (CRM) systems, marketing automation tools, enterprise resource planning (ERP) systems, application programming interfaces (APIs), and cloud services. It is important to understand how each source can be used to inform business decisions and how to integrate the data from each source into the organization’s data landscape.
Once the relevant data sources are identified, organizations should then create an integration and automation system. This system should include a robust interface that allows data to be easily transferred from one system to another. It should also include pre-built integration templates that reduce the coding required and streamline the automation process. Finally, the integration system should be scalable to accommodate different software applications and data types.
Identifying Relevant Data Sources
Having established a data strategy and automated processes, it is now time to identify relevant data sources to drive the integration and automation process. The challenge of data integration lies in identifying the most relevant data sources and understanding how they interact with one another. By doing this, organizations can ensure they are making the most of their data.
Organizations can identify relevant data sources by:
- Understanding the data landscape: Organizations must identify what data exists, where it resides, and how it can be used to support business objectives. They should also identify which data sources are most valuable to the organization.
- Establishing a single source of truth: Organizations should work to establish a single source of truth for their data. This will ensure that all data is accurate and up to date, and can be used to power automation and integration processes.
- Mapping and transforming data: Organizations must understand the structure of their data and how it can be used to power automation and integration processes. They should also identify how different data sources can be connected and transformed into a single, unified source of data.
Once organizations have identified which data sources are most important, they can start to build a robust integration system. This will enable them to automate processes, improve efficiency, and maximize their data.
Building a Robust Integration System
The path to building a robust integration system begins with the recognition that automation and integration are two sides of the same coin. Automation and integration provide the necessary tools to facilitate data flow between different software applications, making it easier to transfer data from one system to another. The key to successful integration and automation is to identify and leverage the strengths of both, and then use them to create a holistic automation approach that can be used to connect different systems and applications.
At the core of integration and automation is the establishment of a data strategy. This strategy should include the identification of relevant data sources, the development of a robust integration system, and the use of specific tools and technologies to achieve the desired outcomes. Integration and automation also involve the use of mapping and transformation, application programming interfaces (APIs), and other technologies to facilitate data transfer.
Organizations often use integration platforms, such as iPaaS and RPA, to streamline and automate the integration process, as well as pre-built integration templates and connectors to connect different applications. It is also important to consider the user experience when automating and integrating different systems and applications. Organizations should leverage the benefits of automation and integration to create a seamless experience for their customers and employees.
Data Security Best Practices
As Chief Data Security Officer, it is important to understand the importance of data security best practices, such as establishing data protection policies, implementing access controls, and maintaining data privacy. Automation and integration become increasingly important in today’s digital landscape. Utilizing tools like application programming interfaces (APIs), integration platforms, and robotic process automation (RPA) can streamline business processes, and provide a competitive edge for organizations.
Integration tools can connect different software applications, while automation tools can automate processes to improve efficiency. Integration and automation are two sides of the same coin; they are both needed to benefit from the advantages of automation.
Establishing Data Protection Policies
Data Security Best Practices are of utmost importance in today’s digital landscape, and establishing data protection policies is a critical first step in the process. The policy should define the data that needs protection, as well as the measures that need to be taken to safeguard it. Such measures can include access controls, encryption and authentication protocols, and compliance with industry standards. It is also essential to consider how data is shared with external stakeholders, and how user data is collected, used, and stored.
In order to ensure data security, organizations must define user roles and permissions, and develop access control protocols that limit the level of access granted to different user groups. This includes establishing a process for verifying user credentials and granting access only to those with the appropriate level of authorization. Additionally, organizations should ensure that access to data is logged and monitored to detect any unauthorized activities.
Organizations should also consider the use of encryption to secure data in transit and at rest. Encryption is a form of data protection that scrambles information, making it unreadable to anyone without the correct key. Similarly, authentication protocols can be used to verify that users accessing sensitive data are who they claim to be. By making use of two-factor authentication, organizations can further strengthen the security of their data.
Implementing Access Controls
Having discussed integration best practices, the next step is to implement access controls to ensure data security best practices. Secure access control is a cornerstone of data security, as it limits access to sensitive data and systems, and accounts for who is doing what, when, and from where. To implement access control, organizations should establish data protection policies, determine when and why access should be granted or denied, and communicate these policies to all users.
Organizations should ensure that all users have an individualized access control policy that describes what they can and cannot do with data. Access control policies should be tailored to the specific user needs, roles, and responsibilities, and should be updated regularly to reflect the organization’s changing needs. Access controls should also be updated to address any changes in the technology that the organization is using.
In addition to setting policies, organizations should also ensure that users have the right level of access. Access controls should be implemented to ensure that users are only granted access to the data they need to do their jobs. This includes both physical and logical access control, such as using secure passwords, two-factor authentication, and encryption. Organizations should also implement identity and access management tools to help manage user access and monitor user activity.
Maintaining Data Privacy
Having established data protection policies and implemented access controls, data privacy is the next essential step to ensure the security of sensitive data. Data privacy involves protecting the confidentiality, integrity, and availability of data while it is in transit or stored, and requires organizations to consider the management of data in terms of access, storage, and transmission. Achieving privacy requires organizations to take several steps such as designing secure data storage systems, encrypting data, and regularly updating the security settings.
Organizations can also benefit from using integration and automation tools to securely transfer data between different applications. Automation and integration tools enable organizations to connect different software applications, sync data across different systems, and create pre-built integration templates to streamline the process of transferring data from one system to another. A reliable integration platform also provides powerful API management capabilities to ensure data is securely transferred from one side of the organization to the other.
Robotic Process Automation (RPA) and Enterprise Service Bus (ESB) are also increasingly important components of data privacy. RPA tools enable organizations to automate processes and improve efficiency, while ESB solutions provide an application programming interface (API) to connect different applications and data sources.
Benefits of Automation and Integration for Data Security
As Chief Data Security Officer, I recognize the numerous benefits of automation and integration for data security. Automated Access Controls, Automated Encryption, and Automated Breach Detection are just a few of the ways businesses can leverage automation and integration to bolster their data security. Integration solutions such as APIs, end-to-end process automation, and workflows, allow businesses to connect different software applications and streamline their business operations. Integration and automation become increasingly important in today’s digital landscape, as organizations often need to sync data across different systems.

Automated Access Controls
The benefits of adopting automation and integration for data security extend to automated access controls which are especially important for organizations that must handle large volumes of data or have many users. Automated access controls can streamline the implementation of security protocols and provide a higher level of governance to ensure that all users are following the same security protocols. Automated access controls ensure that users are not given access to resources they are not supposed to have, while at the same time providing an easy way for users to access resources they need.
Organizations can benefit from automation and integration solutions that can help them connect different systems, sync data across multiple systems, and automate the integration process. Integration Platform as a Service (IPAAS) solutions provide a fast and reliable way to integrate data from one system to another without coding required. Robotic Process Automation (RPA) is another tool that can help organizations automate and integrate their business processes, while Etl (Extract Transform Load) tools can help organizations extract data from disparate sources and load it into a single source of truth.
Using pre-built integration templates and connectors, organizations can quickly and easily integrate different software applications and become more efficient in their business operations.
Automated Encryption
The benefits of automated encryption for data security are numerous. With automated encryption, organizations are able to achieve a level of data security that is far more efficient than manual encryption processes. Organizations can implement automated encryption with the help of integration and automation tools, allowing them to quickly and effectively encrypt data across multiple systems and applications. Automated encryption also makes it easier for organizations to comply with industry regulations, providing an additional layer of security.
Automated encryption helps organizations to protect their data from unauthorized access and eliminate the need for manual encryption processes. Automated encryption can also help organizations to streamline their data security processes, as it eliminates the need for manual entry of encryption keys. Automated encryption also makes it easier to keep track of encryption keys, as they can be securely stored in an automated system.
Integrating automated encryption with other security processes such as access control and breach detection can provide a more comprehensive security solution. For example, when automated encryption is integrated with access control, organizations can ensure that data is only accessible to authorized users and that access is revoked when users no longer need it. Additionally, automated encryption can be integrated with breach detection systems to ensure that any unauthorized access to data is quickly detected and addressed.
Automated Breach Detection
Transitioning from best practices, one of the biggest benefits of automation and integration for data security is the ability to automate breach detection. With automated breach detection, businesses can keep their data secure and prevent costly security incidents from occurring. Automated breach detection takes the burden off of security experts and allows them to focus on other areas of security.
When it comes to automated breach detection, there are three main components:
- Monitoring: This involves monitoring for suspicious activity and alerting the security team to any potential threats.
- Detection: This involves using algorithms and analytics to detect any potential breaches before they occur.
- Remediation: This involves taking action to remediate any security incidents that occur.
Automated breach detection can be used to detect malicious activity, such as malware, phishing attempts, and other malicious activities. Additionally, it can be used to detect unauthorized access to data and systems and can help to ensure that any potential breaches are properly addressed.
Organizations can use automated breach detection to proactively identify and address security threats. This can help to reduce the risk of a breach occurring, as well as reduce the cost and time associated with responding to a breach.
Conclusion
Automation and integration are key components of a successful data security strategy. By leveraging automation and integration, organizations can effectively streamline their processes and safeguard their data. Automation helps to manage data more securely, efficiently, and cost-effectively, while integration ensures that data is accessed in a secure and controlled manner.
Automation and integration best practices must be adopted to ensure data security, while data security best practices must be followed in order to prevent data breaches. In conclusion, automation and integration can play an important role in helping organizations protect their data and maintain data security.