How to Implement Cloud-Based Email Protection for Your Business
AI Overview:
Email remains the number one cyberattack vector, and the stakes have never been higher. In 2023 alone, the FBI’s IC3 report logged nearly 320,000 email-related complaints and over $4.6 billion in losses, much of it tied to Business Email Compromise (BEC). Standard email defenses, like Microsoft 365’s built-in filters, are missing nearly 47% of advanced threats—leaving businesses exposed.
Cloud-based email protection addresses this gap by applying AI and machine learning to detect, block, and remediate threats before they reach your employees. This guide breaks down why modern businesses can no longer rely on legacy email filters and how cloud-based solutions deliver layered, AI-driven defense.
Cloud-based Email Protection: Ultimate Guide 2025
Why Your Business Needs Cloud-Based Email Protection Now
Cloud-based email protection is a security service that filters emails using advanced AI and machine learning to block threats like phishing, malware, and business email compromise (BEC) attacks before they reach your inbox.
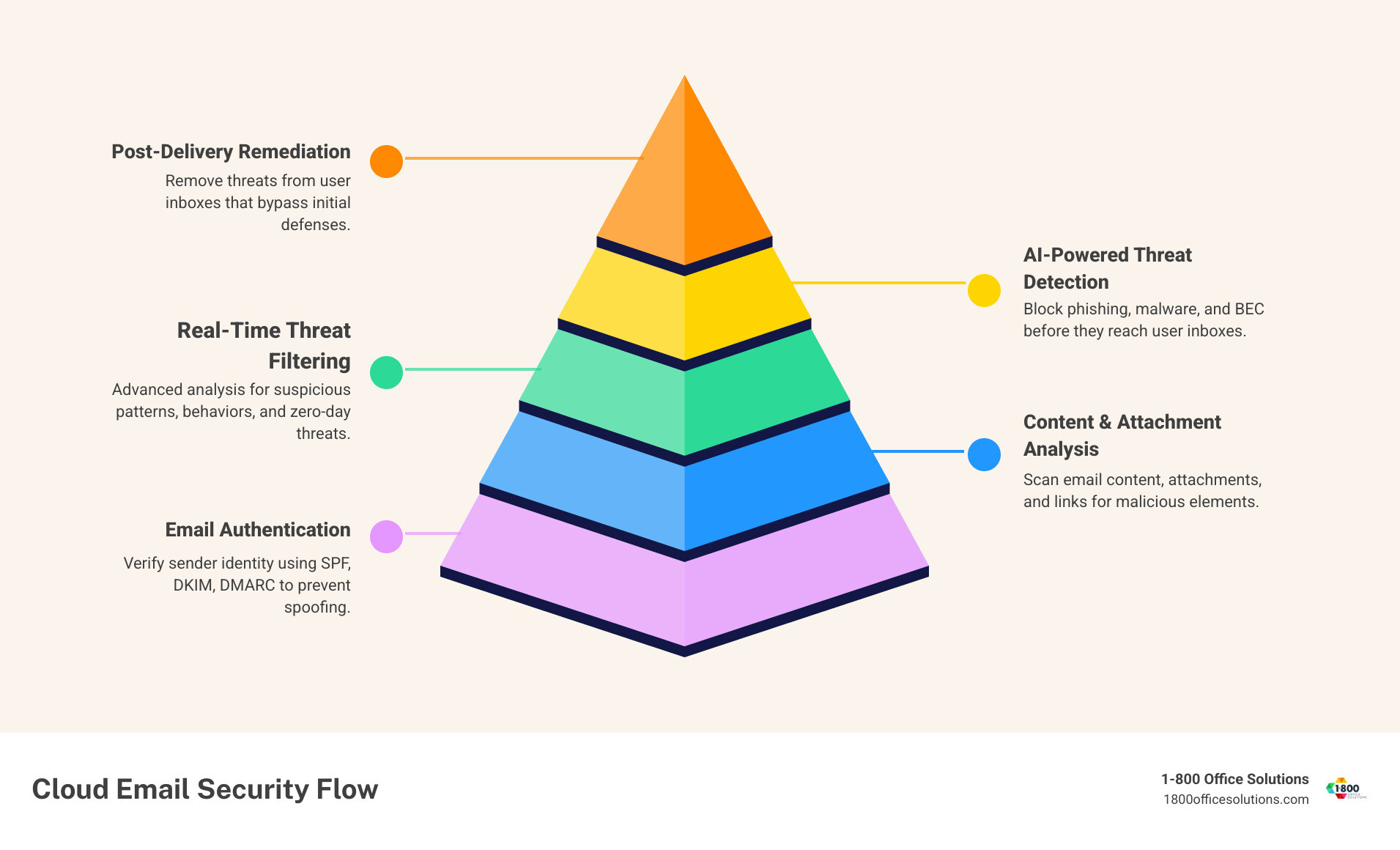
Key Components of Cloud-Based Email Protection:
- AI-powered threat detection – Scans for suspicious patterns and behaviors.
- Real-time filtering – Blocks threats before they reach users.
- Multi-layered defense – Combines multiple security technologies.
- Post-delivery remediation – Removes threats that slip through initial screening.
- Authentication protocols – Verifies sender identity (SPF, DKIM, DMARC).
The FBI’s latest IC3 report reveals a stark reality: advanced email attacks led to nearly 320,000 complaints and over $4.6 billion in losses in 2023. Compounding this, research shows that standard email defenses, like those in Microsoft 365, miss 47% of threats that advanced solutions catch.
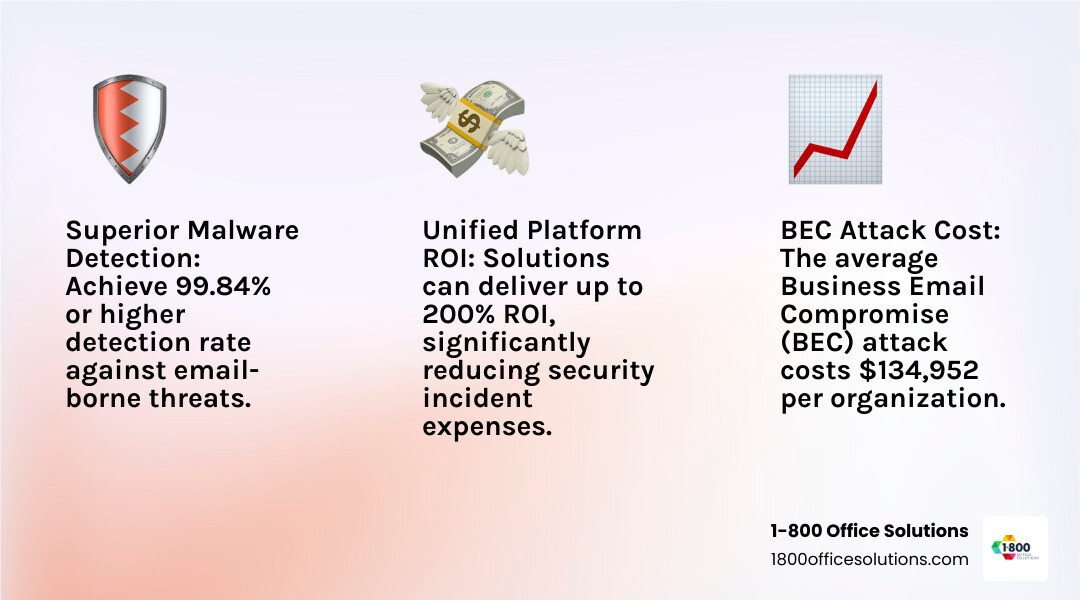
For office managers balancing budgets and IT, the stakes are high. A single successful BEC attack costs an average of $134,952 per organization. Modern cybercriminals use sophisticated social engineering and AI-generated content that bypasses traditional defenses. Cloud-based email protection is essential, acting as an expert security team analyzing every email before it reaches your staff.
This guide covers everything you need to know to implement robust email protection for your business.
Understanding the Modern Email Threat Landscape
Today’s email threats are sophisticated, personalized, and highly effective. Cybercriminals have moved beyond obvious scams to exploit human trust and urgency, making email the number one attack vector, as confirmed by The FBI’s latest IC3 report on cybercrime losses.

Phishing attacks now mimic legitimate communications with convincing branding and timely content, casting a wide net to steal credentials or trick users into clicking malicious links.
Spear phishing is a more precise threat. Attackers research targets on LinkedIn and company websites to craft authentic-looking emails that exploit knowledge of your organization’s structure, vendors, and communication style.
Business Email Compromise (BEC) is the most financially damaging threat, contributing to over $4.6 billion in losses in 2023. These attacks involve impersonating executives to request urgent, fraudulent wire transfers, exploiting workplace hierarchies and a sense of urgency.
Malware delivery has also evolved. Instead of suspicious attachments, malware now hides in seemingly innocent PDFs or Word documents. Ransomware, which can paralyze a business, often originates from an email.
Other quiet threats include data exfiltration, which siphons sensitive information from compromised accounts, and social engineering, which manipulates employees into compromising security. As detailed in More info about persuasive phishing emails, these attacks are incredibly convincing.
Because these threats are often combined, traditional email filters are no longer sufficient. You need cloud-based email protection with AI-powered detection to analyze and stop attacks at the same level of sophistication with which they are created.
How Advanced Cloud-Based Email Protection Works
Cloud-based email protection acts as a digital security checkpoint, using multiple layers of defense to analyze every email for threats. This proactive approach combines AI, real-time threat intelligence, and post-delivery monitoring to catch what basic filters miss. Each layer targets different threats, creating a comprehensive security shield. What is Cybersecurity?
The Role of AI and Machine Learning in Detection
Modern email protection uses AI to learn your organization’s normal communication patterns, achieving up to 99.99% accuracy in catching phishing. It analyzes hundreds of email factors, from sender reputation to message timing, to identify suspicious activity.
- Behavioral analysis learns your email patterns, such as typical senders and communication styles. It flags deviations, like an unusual wire transfer request from a CEO’s account.
- Anomaly detection spots subtle inconsistencies that humans miss, such as an email sent at an odd time or a sender’s writing style not matching their history. This is highly effective against social engineering.
- Natural Language Understanding (NLU) helps the AI grasp the intent behind words, distinguishing a legitimate urgent request from a fraudulent one.
This AI-driven approach is crucial for catching zero-day threats—new attacks that have no known signature. By learning and adapting, these systems can identify suspicious patterns in novel attack methods. Advanced language models can also summarize threats to help security teams understand attack patterns faster.
Foundational Security: Email Authentication Protocols
Before AI analysis, foundational protocols verify a sender’s identity to prevent domain spoofing.
- Sender Policy Framework (SPF) lets domain owners list authorized mail servers. If an email from “yourbank.com” comes from an unauthorized server, it’s flagged.
- DomainKeys Identified Mail (DKIM) adds a digital signature to emails, acting as a tamper-evident seal to prove the message hasn’t been altered.
- Domain-based Message Authentication, Reporting, and Conformance (DMARC) builds on SPF and DKIM. It tells servers how to handle failed authentication checks (e.g., quarantine or reject) and provides reports on potential domain spoofing.
Beyond the Inbox: Post-Delivery Remediation and Response
No system is perfect, so post-delivery protection is vital for handling threats that slip through.
- Automated threat removal can instantly retract a malicious email from all user inboxes after it has been delivered, dramatically reducing the attacker’s window of opportunity.
- Incident investigation tools allow security teams to trace the spread of a malicious email, identify all affected users, and understand the attack’s scope.
- User-reported phishing analysis enables employees to flag suspicious emails with a single click, triggering an automated analysis and potential organization-wide remediation.
Rapid response capabilities are key to minimizing damage from a security incident. Cybersecurity: Cyber Incident Response
A Step-by-Step Guide to Implementing Your Solution
Deploying cloud-based email protection can be a smooth process with the right plan, allowing you to upgrade security without disrupting daily operations. This roadmap will guide you through each step.
Step 1: Assess Your Current Email Security Posture
First, take an honest look at your current email security to identify gaps. Are sophisticated phishing attempts getting through? Do you know what threats your current system is missing?
If you rely on the native security in Microsoft 365 or Google Workspace, you may have significant gaps. These platforms offer baseline protection but are not designed for advanced threats. Specialized solutions detect nearly half of the threats that these built-in defenses miss.
Your risk assessment should clarify the potential cost of an attack, including financial loss (the average BEC attack costs $134,952), lost productivity, and reputational damage. This assessment justifies the investment in a robust cloud-based email protection solution and helps you create effective IT Security Policies Your Company Needs.
Step 2: Choose the Right Deployment Model for Your Cloud-Based Email Protection
Next, select a deployment model that fits your email setup.
- API-based integration is the modern approach. It connects directly to your email system to scan messages after they arrive but before they are opened. A key advantage is that you don’t need to change MX records, simplifying setup. These solutions can also remove threats post-delivery.
- Inline deployment is the traditional route, acting as a gateway that all email must pass through. This requires changing your MX records to route mail through the protection service first. It offers complete control but makes your email flow dependent on the service’s availability.
- Hybrid models combine inline filtering for external mail with API-based scanning for internal traffic and post-delivery remediation.
For most businesses, API-based or hybrid approaches are ideal due to their ease of implementation and advanced features.
Step 3: Integrate with Your Existing Email Platform
Connecting your new cloud-based email protection to your email system is the final step.
- For Microsoft 365, integration typically involves granting specific permissions via Azure AD, allowing the solution to scan emails and act on threats. Reputable providers offer clear, step-by-step guides.
- Google Workspace users follow a similar process, granting permissions through the Google Cloud Platform to enable email monitoring.
Review the permissions you grant to ensure they align with your security policies. You may also need to configure mail flow rules to ensure smooth operation. Quality providers offer support during this phase, and a managed IT service provider can handle the technical details for you. For more information, see Advanced Anti-Phishing Features for Gmail.
Key Features to Look for in a Cloud-Based Email Protection Solution
When choosing a cloud-based email protection solution, focus on its threat protection capabilities, data security features, and overall cost-effectiveness.
Core Threat Protection and Advanced Capabilities
The primary question is: how well does it stop threats? Look for solutions with 99.99% phishing detection accuracy to catch sophisticated BEC, multi-channel, and link-based attacks. A high malware detection rate (99.84% or higher) is also critical for identifying zero-day threats and ransomware.
Given that the average BEC attack costs $134,952, strong BEC protection is essential. The best solutions use AI to analyze language and sender behavior to stop impersonation and fake invoice schemes.
Your protection should also defend against multi-channel attacks that combine email with messaging apps like Slack or Teams. Finally, ensure it has advanced link protection that rewrites and analyzes URLs at the time of click, as malicious sites can change after an email is sent.
Data Loss Prevention (DLP) and Compliance
Your solution must also prevent sensitive data from leaving your organization. Data Loss Prevention (DLP) capabilities should automatically identify and block emails containing sensitive information like credit card numbers or proprietary data. Learn more about Email Data Loss Prevention.
For regulated industries, compliance support for standards like HIPAA, GDPR, or SOX is non-negotiable. Look for features like content filtering, email encryption, and detailed audit trails. Seamless encryption should automatically protect confidential emails without extra steps for your team.
Outbound email protection is also important to prevent your systems from being used to send spam, which protects your company’s reputation.
Evaluating Cost, ROI, and the Power of a Unified Platform
While cloud-based email protection is an investment, its return on investment (ROI) is significant. The Total Cost of Ownership (TCO) is often lower when you factor in avoided breach costs and reduced IT management time, with some businesses seeing 200% ROI in the first year.
A unified platform is a game-changer, combining tools for anti-phishing, archiving, and DLP into a single interface. This simplifies management and improves security effectiveness compared to using multiple separate solutions.
| Feature | Unified Platform | Multiple Point Solutions |
|---|---|---|
| Management | Centralized control, single interface | Separate consoles, fragmented management |
| Integration | Seamless, designed to work together | Manual integration, potential compatibility issues |
| Threat Visibility | Holistic view across all security layers | Siloed views, harder to correlate threats |
| Cost | Often lower TCO, simplified licensing | Higher TCO, complex licensing, vendor management overhead |
| Effectiveness | Coordinated defense, faster response, AI leverages broader data | Gaps in coverage, slower response, potential for threats to slip between solutions |
| Complexity | Reduced for IT teams, streamlined workflows | Increased for IT teams, more training required |
A unified platform not only protects better but also makes your entire operation more efficient.
Creating a Human Firewall: The Role of User Training
Advanced technology isn’t enough; your employees are a critical part of your defense. A “human firewall” is essential because even the best security can be bypassed by human error. Your team is both a potential vulnerability and your strongest line of defense.

User awareness training is the foundation. Regular, interactive sessions that show real-world examples help your team recognize phishing attempts. They learn to spot red flags, like urgent requests from external “executive” accounts or emails with subtle domain misspellings.
Phishing simulations provide hands-on practice in a safe environment. These tests send realistic but harmless phishing emails to employees and offer immediate feedback to those who click, creating learning opportunities without real-world consequences.
Make it easy for employees to report suspicious emails. Many cloud-based email protection solutions include a simple “report phishing” button in the email client. This action can trigger an automated analysis and protective measures across the organization. Find more tips in Simple Ways to Protect Your Email Account.
Building a strong security culture makes cybersecurity everyone’s responsibility. This includes promoting the use of strong, unique passwords and multi-factor authentication (MFA). According to CISA, these are two of the most critical steps an organization can take to protect its communications. CISA guidance on cybersecurity awareness
When you combine robust cloud-based email protection with ongoing user education, you create a multi-layered defense where technology and trained employees work together to keep your business safe.
Frequently Asked Questions about Cloud-Based Email Protection
Here are answers to common questions about cloud-based email protection.
What's the difference between a Secure Email Gateway (SEG) and an API-based solution?
A Secure Email Gateway (SEG) is a traditional, inline solution that acts as an external checkpoint. It requires changing your MX records to route all email through its filters before it reaches your server.
An API-based solution is a modern, out-of-band approach that connects directly to your cloud email provider (like Microsoft 365). It scans emails after delivery but before they are opened, doesn't require MX record changes, and can remove threats retroactively. This makes deployment easier and provides deeper insights into internal threats.
Can cloud email security stop zero-day attacks?
Yes. This is a key strength of modern solutions. Instead of relying on known threat signatures, they use AI and machine learning to identify suspicious behavior in new, never-before-seen attacks. Sandboxing technology further improves this by safely executing suspicious attachments and links in an isolated environment to observe their behavior. This proactive approach, combined with behavioral analysis and heuristics, is highly effective against zero-day threats.
How does cloud email security protect against Business Email Compromise (BEC)?
BEC attacks rely on social engineering and impersonation, often without any malicious links or attachments. Cloud-based email protection combats these threats using sophisticated AI analysis of language and context. The system learns the typical communication styles of your executives and flags anomalies, such as unusual language or urgent wire transfer requests.
Anomaly detection also identifies behavioral red flags, like emails sent at odd hours or requests that bypass normal approval channels. This multi-layered analysis is effective at stopping supplier invoicing fraud and executive impersonation, justifying the investment when a single BEC attack costs an average of $134,952.
Conclusion
Email security is no longer an optional IT task; it’s a critical investment in your business’s survival. Traditional, passive approaches are insufficient against today’s sophisticated threats. As we’ve covered, a multi-layered cloud-based email protection strategy is essential to fight back with advanced AI and machine learning.
Implementing this technology is far easier than recovering from a cyberattack, which can cost an average of $134,952 for a single BEC incident. The roadmap we’ve outlined—assessing your posture, choosing a deployment model, and integrating with your platform—provides a clear path forward.
However, technology alone is not a complete solution. Your employees are your first line of defense. Combining cutting-edge cloud-based email protection with a well-trained team creates a security culture that is incredibly difficult for cybercriminals to penetrate.
The ROI is clear, with businesses seeing returns of up to 200% from preventing attacks and gaining operational efficiency with a unified platform.
Don’t let email be the weak link in your business. At 1-800 Office Solutions, we understand the unique needs and budget constraints of businesses like yours. We’re here to help you steer the complexities of email security and find the right solution.
Secure your business with comprehensive email security solutions