Cloud Security Assessments: A Guide to Uncovering Risks and Fortifying Your Cloud
A comprehensive cloud security assessment provides a systematic review of your cloud accounts, services, and security controls. Its primary purpose is to identify misconfigurations, vulnerabilities, and policy gaps before they can be exploited. This is more than a simple scan; it delivers a clear, prioritized roadmap to strengthen your defenses against sophisticated cyber threats and ensure your cloud environment is both secure and resilient.
Why Cloud Security Assessments Are Essential

Managing security within a sprawling cloud environment presents a significant challenge. The same agility that allows businesses to rapidly deploy new services can also introduce hidden risks, from exposed data storage to user accounts with excessive permissions. A cloud security assessment acts as your essential reality check, enabling you to find and remediate these weak spots before an attacker does.
Think of it as a structural inspection for a high-value commercial property. You wouldn’t rely on a superficial glance; a proper evaluation meticulously examines the foundation (your cloud configuration), the locks on every door (access controls), and all potential entry points (vulnerabilities). This process is fundamental to protecting your organization’s most valuable digital assets.
Protecting Your Business Operations
Unchecked cloud vulnerabilities can disrupt your business operations, leading to downtime, financial loss, and significant reputational damage. By proactively identifying security gaps, you can prevent incidents that could otherwise cripple your business.
These assessments are also critical for maintaining the trust of clients and partners. Demonstrating a robust security program sends a clear message: protecting customer data is a top priority. A solid grasp of Cloud Security Fundamentals is the first step in building this trust. This guide will walk you through the entire assessment process, from understanding the different types to implementing the findings effectively.
A cloud security assessment is not merely a technical exercise; it’s a strategic business imperative. It provides the clarity needed to make informed decisions, allocate resources effectively, and build a resilient security posture that supports long-term growth.
The Core Benefits of a Thorough Assessment
The value of regular cloud security assessments extends beyond simply patching vulnerabilities. It provides a strategic advantage by ensuring your security investments align directly with business objectives.
Here are the key benefits you can expect:
- Improved Security Posture: Directly address misconfigurations and vulnerabilities, making your environment a significantly harder target for attackers.
- Enhanced Compliance Adherence: Generate the concrete evidence required to satisfy auditors for frameworks like HIPAA, PCI DSS, and SOC 2.
- Reduced Risk of Data Breaches: Proactively close the security gaps that could lead to the exposure of sensitive customer or corporate data.
- Increased Visibility: Gain a clear, comprehensive map of your entire cloud environment, including all assets and their configurations.
Ultimately, a well-executed assessment provides the actionable intelligence needed to protect your digital infrastructure and secure your future.
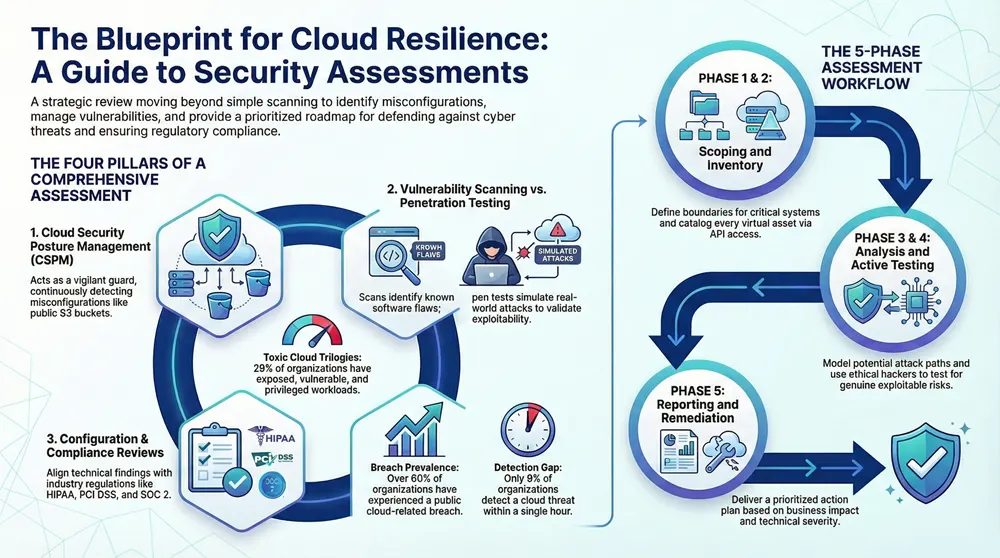
The Four Pillars of an Effective Assessment
An effective cloud security assessment is not a single scan but a coordinated effort built on four distinct pillars. Each provides a unique perspective on your security posture. When combined, they offer a complete, multi-layered view of your cloud environment’s true risk profile.
This is analogous to a full diagnostic on a high-performance vehicle. One technician checks the engine (workloads), another inspects the electrical system (configurations), a third conducts a road test to evaluate performance under pressure (penetration testing), and a fourth verifies compliance with safety standards. All four are necessary to confirm the vehicle is road-ready. Let’s break down each essential component.
1. Cloud Security Posture Management (CSPM)
The first pillar is Cloud Security Posture Management (CSPM). As the bedrock of your assessment, it is designed to discover and remediate misconfigurations across your cloud services. CSPM tools act like a vigilant security guard, continuously patrolling your environment and comparing every configuration against established best practices.
A common and critical example is an Amazon S3 bucket inadvertently left open to public access, exposing sensitive data. CSPM automates the detection of such errors. This is where strong IT asset management best practices are non-negotiable; you cannot secure what you do not know you have.
2. Vulnerability Scanning
While CSPM focuses on cloud infrastructure, vulnerability scanning examines the assets within it. This process identifies known software flaws—the Common Vulnerabilities and Exposures (CVEs)—in your operating systems, applications, and containers. It is like checking the locks on your doors to ensure they do not have a known manufacturing defect that could be easily exploited.
For instance, a vulnerability scan could flag a web server running an outdated version of Apache with a well-documented security flaw. This is a significant risk, as cybercriminals use automated tools to find and exploit such low-hanging fruit to gain an initial foothold. For a deeper dive, explore our guide on protecting your cloud security workloads.
Comparing Key Cloud Security Assessment Types
To better understand how these assessments work together, it is helpful to compare them side-by-side. Each plays a unique and critical role in building a comprehensive defense.
| Assessment Type | Primary Focus | What It Uncovers | Best For |
|---|---|---|---|
| CSPM | Cloud service & infrastructure configuration | Misconfigurations, compliance drifts, overly permissive access (e.g., public S3 buckets) | Gaining foundational visibility and enforcing baseline security across the cloud. |
| Vulnerability Scanning | Known software flaws within workloads | Outdated software, missing patches, known exploits (CVEs) in applications and OS. | Identifying specific, documented weaknesses inside your virtual machines and containers. |
| Cloud Penetration Testing | Real-world exploitability of your defenses | Actionable attack paths, chained exploits, business logic flaws, actual security gaps. | Validating if your security controls can withstand a simulated, real-world attack. |
| Configuration Review | Adherence to specific compliance frameworks | Gaps against standards like HIPAA, PCI DSS, SOC 2; policy & procedure weaknesses. | Preparing for audits and proving compliance to regulators or clients. |
Ultimately, a strong security program does not choose one over the other but layers these assessments to cover all angles—from automated configuration checks to hands-on adversarial testing.
3. Cloud Penetration Testing
The third pillar, cloud penetration testing, is an active, adversarial exercise where ethical hackers simulate a genuine cyberattack on your cloud environment. Their mission is to find and exploit the vulnerabilities and misconfigurations identified by other tools to determine how far an attacker could penetrate your defenses. It serves as the ultimate stress test.
A penetration test doesn’t just find problems; it demonstrates their impact. It moves beyond “What if?” to answer the critical question: “If an attacker targeted us right now, what real damage could they do?”
An ethical hacker might chain a minor configuration error with a low-priority vulnerability to achieve full administrative access—a complex attack path that automated tools would almost certainly miss.
4. Configuration and Compliance Reviews
Finally, the configuration and compliance review ties all technical findings back to the specific regulations you must follow, such as HIPAA, PCI DSS, or SOC 2. This review extends beyond technical settings to examine policies, access control procedures, and documentation to ensure you meet the stringent demands of your industry.
This meticulous, line-by-line audit produces the evidence needed to satisfy auditors. The stakes are high. The Tenable Cloud Security Risk Report reveals that 59% of organizations view insecure identities and permissions as their greatest threat. Furthermore, 29% of organizations face “toxic cloud trilogies”—workloads that are publicly exposed, critically vulnerable, and highly privileged. This review helps prove your organization is not one of them.
Your Step-by-Step Cloud Assessment Workflow

A structured cloud security assessment is a methodical process, not a series of random scans. By breaking the engagement into clear, manageable phases, you can transform an overwhelming technical audit into a straightforward project with clear objectives.
The workflow follows a logical path, from defining what you aim to accomplish to developing a concrete, actionable plan to enhance your cloud environment’s security. Each step builds upon the last, ensuring a thorough and comprehensive review. This diagram illustrates how the core pillars—posture management, vulnerability scanning, and penetration testing—work in concert.
As shown, the process is interconnected through continuous monitoring, asset identification, and finding validation, forming a complete cycle rather than a one-time task.
Phase 1: Scoping and Planning
The first and most critical step is Scoping and Planning. In this phase, you and the assessment team define the engagement’s boundaries. Since it is impractical to test everything at once, the goal is to focus on your most critical systems and significant risks.
During this phase, we establish answers to key questions:
- Which specific cloud accounts (AWS, Azure, GCP) are in scope?
- Are there certain applications or databases that are critical to include?
- What is the primary driver for the assessment, such as preparing for a HIPAA audit?
Defining the scope accurately from the outset ensures the assessment remains focused on what matters most to your business.
Phase 2: Information Gathering
With the boundaries established, the team proceeds to the Information Gathering phase. The objective is to build a detailed map of your cloud environment. Using read-only API access, security analysts catalog every asset within the defined scope.
This involves a complete inventory of your virtual machines, storage buckets, user accounts, security groups, and network configurations. A thorough understanding of your assets is a prerequisite for effective protection.
Phase 3: Threat Modeling and Analysis
Once the environment is mapped, Threat Modeling and Analysis begins. Here, analysts adopt an attacker’s perspective, using the gathered data to identify potential attack paths and theoretical weaknesses.
For example, they might identify a database that, while not directly exposed to the internet, could be accessed from a web server with excessive permissions. This analysis focuses on how minor misconfigurations could be chained together to create a major security breach. Managing these risks is critical, a topic covered in our cybersecurity risk assessment and management guide.
Phase 4: Active Testing and Validation
Next, the process moves from theory to practice in the Active Testing and Validation phase. Here, potential risks are tested to confirm their validity. Automated vulnerability scanners are directed at your systems, and in a penetration test, ethical hackers actively attempt to exploit identified weaknesses.
This phase is what separates the real threats from the “what-ifs.” It provides hard proof of which vulnerabilities are actually exploitable in your environment, cutting through the noise and letting you focus on genuine risks.
Phase 5: Reporting and Remediation
The final step is Reporting and Remediation Planning. The assessment team delivers a comprehensive report detailing every finding, complete with risk scores, evidence such as screenshots, and, most importantly, clear, step-by-step remediation instructions.
An effective report does not merely list problems; it prioritizes them based on business impact and exploitability, providing your team with a clear action plan. This is the ultimate value of the assessment: an actionable strategy to build a stronger, more resilient security posture.
Connecting Assessments to Your Compliance Needs
A cloud security assessment provides much more than technical risk identification; it is a powerful tool for achieving and maintaining regulatory compliance. For any business handling sensitive data, these assessments are a fundamental component of demonstrating due diligence and avoiding the significant penalties associated with non-compliance.
Consider this: a compliance framework like HIPAA or PCI DSS acts as the building code for your digital infrastructure. A cloud security assessment is the official inspection that verifies you have built everything to specification, confirming the structural integrity of your data protection measures.
Mapping Assessments to Major Frameworks
While different compliance standards have unique requirements, they all mandate regular risk analysis and vulnerability management. A well-executed cloud security assessment directly addresses these core requirements, providing auditors with the concrete evidence they need.
Here’s how assessment activities align with common, high-stakes regulations:
- HIPAA (Health Insurance Portability and Accountability Act): The HIPAA Security Rule explicitly requires covered entities to conduct a regular “risk analysis” to safeguard electronic protected health information (ePHI). Vulnerability scans and configuration reviews fulfill this requirement by identifying and evaluating potential risks to ePHI stored in your cloud environment.
- PCI DSS (Payment Card Industry Data Security Standard): Requirement 11 of PCI DSS mandates regular testing of security systems and processes. This includes performing internal and external vulnerability scans at least quarterly and after any significant network change, as well as annual penetration testing, making these activities a non-negotiable prerequisite for compliance.
- SOC 2 (Service Organization Control 2): A SOC 2 report evaluates controls against criteria like Security, Availability, and Confidentiality. Assessments provide hard evidence for the “Security” criterion by demonstrating that your controls are in place and effective at protecting against unauthorized access and system damage.
The Business Case for Compliance-Driven Security
Viewing assessments through the lens of compliance reveals a clear business case. The objective shifts from simply patching security holes to actively reinforcing your company’s legal and operational foundation. This approach helps maintain critical certifications, build trust with customers, and avoid the staggering costs of a compliance failure.
This need is more urgent than ever. A recent report on cloud security statistics indicates that over 60% of organizations have experienced a public cloud-related breach. Compounding the problem is a significant detection lag—only 9% of organizations detect a cloud threat within an hour.
An assessment transforms compliance from a theoretical checklist into a demonstrated reality. It provides tangible proof that you not only have security policies in place but that they are actively working to protect sensitive data against real-world threats.
Aligning cloud security assessments with regulatory needs creates a more efficient and effective security program. This mindset is central to successful compliance process optimization, ensuring security efforts simultaneously reduce risk and support broader business goals. The assessment’s final report becomes a cornerstone document for any audit, proving your commitment to a strong and defensible security posture.
Making Sense of Your Results and Deciding What to Fix First
A high-quality cloud security assessment report is more than a list of deficiencies; it is your strategic blueprint for action. The real value is realized when you translate technical findings into a prioritized plan to address the most critical issues. An effective report bridges the gap between raw data and sound business decisions, providing your team with the clarity needed to act decisively.
To be effective, the report must cater to multiple audiences. It should begin with a concise executive summary that outlines the most significant risks in clear business terms. This is followed by a detailed technical analysis, complete with risk scores, supporting evidence, and practical remediation guidance.
Decoding Your Assessment Report
The first step is understanding the report’s structure. A long list of vulnerabilities without context can be overwhelming and difficult to act upon. The goal of a report should be to deliver clarity, not confusion.
A best-in-class report will always contain these core elements:
- Executive Summary: A high-level overview for leadership, focusing on critical risks and their potential business impact.
- Detailed Technical Findings: The core of the report, documenting each vulnerability or misconfiguration with its location, severity (e.g., Critical, High, Medium), and supporting evidence like screenshots or logs.
- Actionable Remediation Steps: The most crucial section, providing specific, step-by-step instructions on how to resolve each issue, enabling your team to move directly from discovery to resolution.
A Framework for Prioritizing Fixes
Once you understand the findings, the challenge is to determine what to fix first. Addressing every low-level alert can lead to team burnout with minimal security improvement. The key is to prioritize based on real business risk, not just technical severity. A “medium” risk finding that is easily exploitable may be more dangerous than a “critical” one that is nearly impossible for an attacker to reach.
This is where the concept of “toxic risk combinations” becomes invaluable. These are scenarios where several seemingly minor issues align to create a major security vulnerability.
Consider this example:
- A public-facing web server (exposure)
- Running software with a known, unpatched bug (vulnerability)
- And possessing an IAM role with excessive permissions (excessive privilege)
Individually, each might be a medium-risk issue. Together, they create a direct pathway for an attacker to compromise your entire cloud account. The goal is to identify and dismantle these dangerous chains first. This risk-based approach ensures your team’s efforts are focused where they will have the greatest impact.
A successful remediation strategy isn’t about fixing everything at once. It’s about systematically neutralizing the most dangerous attack paths first, breaking the chains that connect minor issues to catastrophic business outcomes.
The Challenge of Interconnected Risks
This prioritization is essential due to the interconnected complexity of cloud environments. In today’s multi-cloud reality, an estimated 33% of all cloud assets are unmanaged, with each carrying an average of 115 vulnerabilities. The problem is magnified when you consider that 13% of organizations have at least one cloud asset that creates over 1,000 potential attack paths. These figures from the State of Cloud Security Report highlight how a single oversight can lead to massive exposure.
By focusing on these toxic combinations, you move beyond a simple to-do list and begin to think strategically about reducing the probability of a major breach. This transforms your assessment report from a daunting list of tasks into a powerful tool for building a more resilient and secure business.
Finding the Right Partner for Your Cloud Security Assessment
Selecting the right security partner is as critical as the assessment itself. The quality of the results, the clarity of the findings, and the practicality of the remediation plan all depend on the expertise of the team you engage. A great partner acts as an extension of your team, offering strategic guidance tailored to your business, not just a list of technical jargon.
Look beyond the sales pitch to evaluate a vendor’s real-world experience, technical capabilities, and communication style. The right firm will have a proven track record not only in security but specifically within your industry and with your chosen cloud platform—be it AWS, Azure, or GCP.
What to Look for in a Vendor
When evaluating potential partners, focus on a few core areas. These criteria will help you determine whether you are hiring a team with the technical depth and professional polish to deliver real value or a firm that simply runs a scanner and provides a generic PDF.
Your evaluation checklist should cover these key points:
- Industry-Specific Experience: Do they understand the unique compliance requirements and threat models of your sector, such as healthcare or finance? A partner familiar with HIPAA or PCI DSS provides a significant advantage.
- Technical Certifications: Verify that their team holds recognized certifications like OSCP, CISSP, or cloud-specific credentials from AWS or Azure. This serves as a baseline for their technical competence.
- Process and Methodology: Request a walkthrough of their assessment workflow. A transparent, methodical process is a strong indicator of a mature and reliable provider.
- Reporting and Communication Style: Always ask for a sanitized sample report. Is it clear and concise? Does it offer actionable, prioritized advice, or is it merely a raw data dump from a tool?
Think of this as a long-term investment in your security program. You’re not just buying a one-time report. You’re building a relationship with a team that can help guide your security strategy long after the assessment is done.
Smart Questions to Ask Potential Partners
To truly assess a potential partner, ask questions that go beyond the surface. The goal is to understand their thought process, work style, and the support you can expect after the project is complete. Arm yourself with questions that get to the heart of their service delivery.
Before signing a contract, ensure you get clear answers to these questions:
- How do you tailor the assessment to our specific cloud environment and compliance needs? A one-size-fits-all approach is a major red flag. They should be able to explain how they will customize the scope to your unique risks.
- Can you walk me through your process for validating findings to eliminate false positives? You want a partner focused on real, exploitable risks, not one who will deliver a 100-page report filled with theoretical or low-impact noise.
- What does your support look like after the assessment? The engagement shouldn’t end with the report. Ask if they offer debriefing calls with your technical team, assistance with remediation questions, or re-testing to verify fixes.
- How do you handle sensitive data you might discover during the assessment? A professional firm will have strict, documented policies for data handling. They should be able to explain exactly how they maintain the confidentiality and security of your information throughout the process.
By asking these pointed questions, you can cut through the marketing fluff and find a true security partner—one with the expertise and commitment to genuinely improve your cloud security.
Common Questions About Cloud Security Assessments
Even with a clear plan, several questions often arise when preparing for a cloud security assessment. To provide clarity, here are straightforward answers to the most common inquiries from business leaders and IT managers.
How Often Should We Conduct an Assessment?
As a general rule, every organization should conduct a comprehensive cloud security assessment at least annually. This regular check-in is crucial for maintaining a strong security baseline and providing an in-depth review of your evolving environment.
However, for businesses in highly regulated industries or those with rapidly changing cloud infrastructures, quarterly assessments are a more prudent approach. Additionally, any significant event—such as migrating a major application to the cloud or onboarding a new provider—should trigger an immediate, targeted assessment to validate security controls from day one.
What Is the Difference Between a Scan and a Pen Test?
This is a common point of confusion, but a simple analogy makes it clear.
Think of it this way: a vulnerability scan is like an automated system checking every door and window in your building to see if they are unlocked. A penetration test is when a security expert actively tries to open those unlocked doors and see how far they can get inside.
A scan provides broad, automated coverage of known weaknesses. In contrast, a penetration test offers deep, real-world insight into how an actual attacker could exploit those weaknesses to compromise your systems.
Are Cloud Security Assessments Necessary for a Small Business?
Absolutely. Attackers often perceive small businesses as easier targets, assuming they have fewer security resources. A single breach can be devastating for a small company, impacting finances, operations, and reputation.
Remember that cloud providers like AWS and Azure operate under a shared responsibility model. They secure the global infrastructure—data centers, servers, and networks—but you are responsible for securing everything you place in the cloud. This includes your data, applications, and user access.
An assessment is the only effective way to ensure you are fulfilling your part of this critical responsibility and protecting your business from preventable threats.
Ready to gain a true understanding of your cloud security posture? The expert team at 1-800 Office Solutions delivers comprehensive cloud security assessments that uncover hidden risks and provide a practical, actionable roadmap for remediation. Protect your business and schedule your assessment today.