The Science of Computer Forensic Analysis: A Deep Dive
Computer forensic analysis is the scientific process of collecting, examining, and analyzing digital evidence from computers and electronic devices to solve crimes or support legal proceedings. It combines computer science with legal forensics to gather evidence that can be used in court.
Key Components of Computer Forensic Analysis:
- Digital Evidence Collection – Preserving data from computers, mobile devices, and networks
- Data Recovery – Retrieving deleted, damaged, or hidden files
- Timeline Analysis – Reconstructing events to understand what happened and when
- Legal Documentation – Creating reports that meet court admissibility standards
- Expert Testimony – Explaining technical findings in understandable terms
The need for computer forensic analysis has exploded alongside our digital dependence. In 2022, the FBI estimated that computer crimes cost Americans $10.3 billion – up from $6.9 billion the previous year. With over 880,000 cybercrime complaints reported in 2023, investigators need scientific methods to track down digital criminals and recover critical evidence.
Unlike cybersecurity (which focuses on prevention), computer forensics is reactive – it investigates what happened after an incident occurs. As one expert noted, computer forensics is “more of an art than a science,” requiring both technical skills and investigative judgment to piece together digital clues.
Whether it’s a corporate data breach, employee misconduct, or criminal investigation, computer forensic analysis provides the foundation for understanding digital crimes and holding perpetrators accountable.
Find more about computer forensic analysis:
Foundations of Computer Forensics
Think of computer forensic analysis as digital detective work. Just like traditional forensics examines fingerprints and DNA, computer forensics examines the digital fingerprints left behind on electronic devices. The primary purpose is straightforward: to identify, preserve, recover, and analyze digital evidence in a way that holds up in court.
But here’s where it gets interesting – computer forensic analysis goes far beyond simply recovering lost files. While your typical data recovery service might help you get back those vacation photos you accidentally deleted, computer forensics is about building a complete picture of what happened, when it happened, and who was involved.
The key difference lies in the approach. Data recovery focuses on getting your information back so you can use it again. Computer forensic analysis, however, treats every bit of data as potential evidence. Every step must be documented, every process must maintain the integrity of the original data, and everything must be legally defensible. It’s the difference between fixing a problem and solving a mystery.
For a deeper dive into the fundamentals, “What Is Computer Forensics?” provides an excellent foundation for understanding this field.
The Evolution from Mainframes to the Cloud
Computer forensic analysis has come a long way since the early days of computing. Back in the 1980s, when personal computers started showing up in homes and offices, criminals quickly figured out they could use these new tools for illegal activities. Law enforcement had to scramble to keep up – suddenly, evidence wasn’t just physical anymore.
The internet changed everything in the 1990s and 2000s. Crimes that once required being physically present could now be committed from thousands of miles away. Hackers could break into systems, steal data, and disappear into the digital ether. This created an entirely new category of investigation that traditional forensics wasn’t equipped to handle.
Today’s digital landscape is even more complex. Your smartphone probably contains more personal information than your entire house did twenty years ago. Internet of Things (IoT) devices are everywhere – your smart thermostat, fitness tracker, even your refrigerator might hold clues to solving a case.
Cloud computing presents perhaps the biggest challenge yet. When data lives “in the cloud,” it’s actually stored on servers that could be anywhere in the world. This creates headaches around jurisdiction, data access, and privacy laws that forensic investigators are still learning to steer.
Each technological leap forward means forensic analysts must constantly update their skills and tools. What worked for investigating crimes on a desktop computer in 2000 won’t cut it for analyzing a modern smartphone or cloud-based attack.
Key Types of Digital Evidence
In computer forensic analysis, digital evidence comes in two main flavors: persistent data and volatile data. Understanding the difference can make or break an investigation.
Persistent data sticks around even when you turn off a device. Think of it as the digital equivalent of fingerprints left on a surface – they remain until someone actively removes them. This includes files on hard drives, photos on your phone, or documents saved to a USB drive. Because this data survives power cycles, investigators have more time to properly collect and analyze it.
Volatile data, on the other hand, disappears the moment you pull the plug. It’s like steam from a hot cup of coffee – there one moment, gone the next. This includes information stored in RAM (Random Access Memory), active network connections, and running processes. Capturing volatile data requires quick thinking and specialized techniques, often working on live systems before they’re shut down.
Digital evidence can hide in surprising places. Hard drives and solid-state drives remain the bread and butter of most investigations, containing operating systems, user files, and even deleted data that can be recovered. Mobile phones are goldmines of personal information – call logs, text messages, photos with location data, and app usage patterns that can reveal someone’s entire daily routine.
Network logs tell the story of digital communications, showing who connected to what, when, and for how long. Cloud storage services like Google Drive or Dropbox add another layer of complexity, requiring specific legal procedures to access data stored on remote servers.
Even RAM can hold crucial evidence – encryption keys, recently accessed files, or traces of malicious software that never touched the hard drive. The key is knowing where to look and how to preserve what you find.

The Digital Investigation: A Step-by-Step Process
When a cybercrime occurs or digital evidence needs to be uncovered, computer forensic analysis follows a methodical, scientific approach that’s as precise as any crime scene investigation. Think of it like being a detective, but instead of fingerprints and DNA, you’re working with deleted files, network logs, and hidden data fragments.
The process isn’t just about finding information—it’s about finding it in a way that will hold up in court. Every single step must maintain what we call the chain of custody, a documented trail showing exactly who handled the evidence, when, and how. One broken link in this chain could render even the most damning evidence inadmissible.
For businesses dealing with data breaches or employee misconduct, understanding this process helps you know what to expect when investigators arrive. The US-CERT overview of computer forensics provides excellent technical details about these procedures.

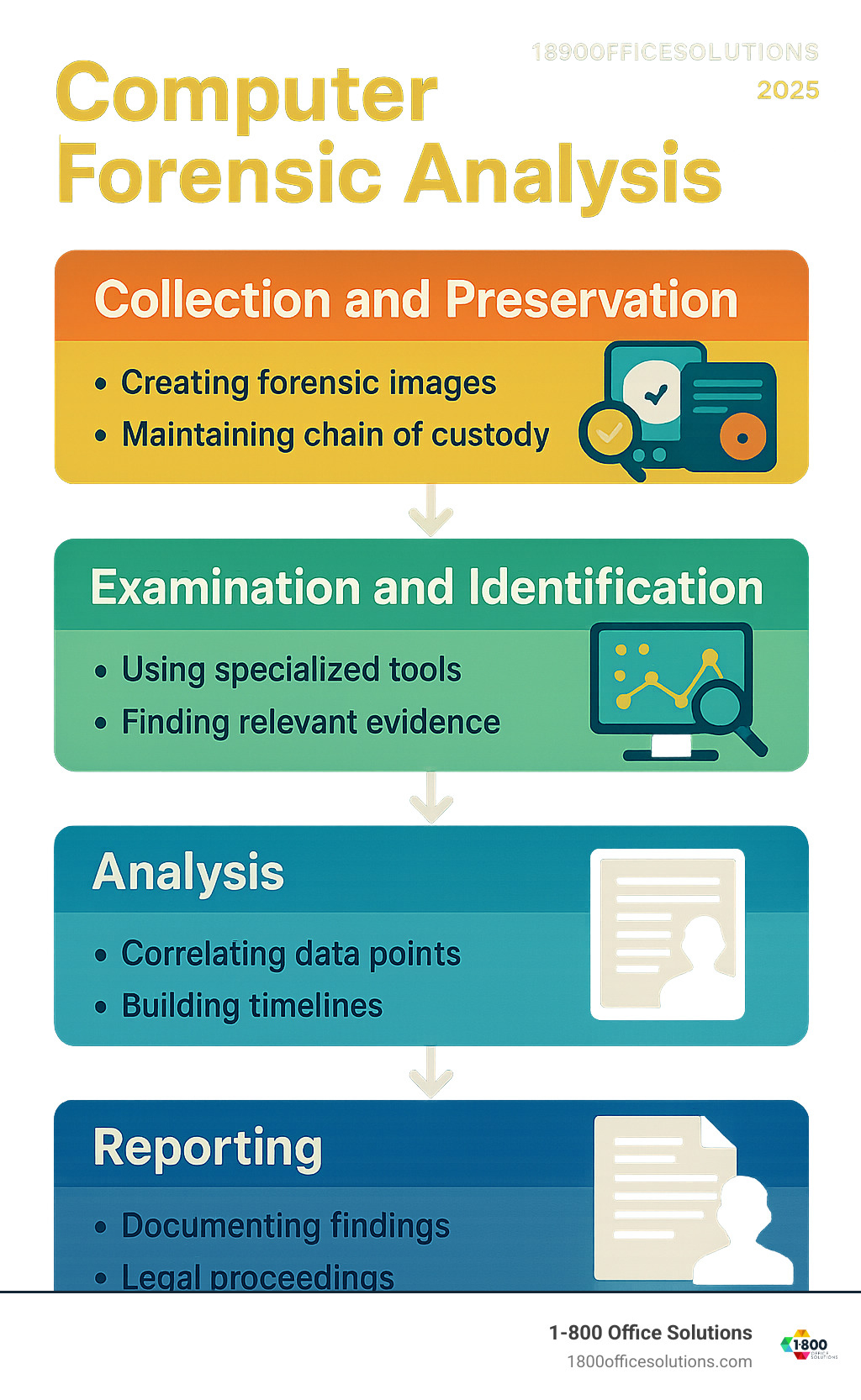
Step 1: Collection and Preservation
The moment investigators identify a device that might contain evidence, the clock starts ticking. This first phase of computer forensic analysis is absolutely critical—any mistake here can destroy evidence or make it legally worthless.
Seizure of devices begins with proper legal authority, whether that’s a search warrant, court order, or written consent. Investigators photograph everything exactly as they found it, noting the position of cables, what was displayed on screens, and even which programs were running. These details might seem minor, but they can be crucial later.
The golden rule of digital forensics is simple: never work on the original. Instead, investigators create what’s called a forensic image—a bit-for-bit copy that captures every single piece of data on the device, including deleted files and empty space. This isn’t like copying files to a backup drive; it’s creating an exact digital twin.
To prevent any accidental changes during this process, write blockers act like a one-way valve. They allow data to flow out of the original device for copying, but absolutely nothing can flow back in. It’s impossible to accidentally modify evidence this way.
Once the forensic image is complete, investigators use hashing algorithms like MD5 or SHA-256 to create a unique digital fingerprint for both the original device and the copy. If these hash values match perfectly, it proves the copy is identical to the original. If even one bit of data differs, the hash values won’t match—providing ironclad proof that evidence hasn’t been tampered with.
Documenting the scene means recording every detail: who was present, what time each action occurred, serial numbers of devices, and the exact procedures followed. This paperwork might seem tedious, but it’s what makes digital evidence legally admissible.
Step 2: Examination and Identification of Evidence
With a perfect copy of the evidence safely preserved, investigators can now dig into the data without any risk of damaging the original. This phase of computer forensic analysis is like archaeological excavation—carefully sifting through layers of digital information to find relevant artifacts.
Specialized forensic tools give investigators superhuman abilities to examine data. These programs can peer into file systems, reveal hidden partitions, and even reconstruct fragments of files that were partially overwritten. The software handles the technical complexity while investigators focus on finding meaningful evidence.
Identifying relevant files requires both technical skill and investigative intuition. Investigators search for documents, emails, photos, videos, and browsing history related to the case. They use keyword searches, filter by date ranges, and look for specific file types. Sometimes the most important evidence hides in seemingly innocent files.
When files are “deleted” on most computer systems, they’re not actually erased—they’re just marked as available space. Data carving recovers these deleted files by searching for recognizable patterns that indicate where files begin and end. It’s like finding torn photographs in a wastebasket and carefully piecing them back together.
File system analysis requires understanding how different operating systems organize data. Windows NTFS systems store information differently than Apple’s file systems or Linux formats. Investigators need to speak all these digital languages fluently to extract evidence properly.
The unallocated space on drives often holds the most interesting evidence. This “empty” space frequently contains remnants of deleted files, temporary data, and other digital breadcrumbs that users thought were gone forever.
Step 3: The Computer Forensic Analysis Phase
This is where raw data transforms into compelling evidence. The analysis phase of computer forensic analysis requires investigators to become digital detectives, connecting scattered clues into a coherent story of what actually happened.
Timeline analysis creates a chronological roadmap of events. By examining timestamps on files, system logs, and user activities, investigators can reconstruct exactly what occurred and when. This timeline often reveals patterns that aren’t obvious when looking at individual pieces of evidence.
In complex investigations, cross-drive analysis compares information from multiple devices—computers, phones, tablets, and external drives. This correlation often reveals connections between suspects, identifies communication patterns, and uncovers evidence that no single device could provide alone.
Steganography detection searches for hidden messages embedded within innocent-looking files. Criminals sometimes hide encrypted communications inside digital photos or audio files. Specialized tools can detect these hidden payloads that would be invisible to casual inspection.
Log file analysis examines the digital breadcrumbs that systems automatically create. These logs record user logins, file accesses, network connections, and system events. They’re like a security camera for digital activities, capturing details that users never realize are being recorded.
The real skill in computer forensic analysis lies in correlating data points from different sources. An email timestamp might align with a file creation time, which corresponds to a network connection log entry. These connections help investigators understand not just what happened, but how and why it happened.
Throughout this process, investigators focus on answering the fundamental questions: Who was responsible? What exactly occurred? When did each event happen? Where did activities take place? How were they accomplished? This systematic approach ensures nothing important gets overlooked.
Step 4: Reporting and Presentation
The most sophisticated computer forensic analysis means nothing if the findings can’t be clearly communicated to non-technical audiences. This final phase translates complex technical findies into reports that lawyers, judges, and juries can understand and trust.
Formal report creation follows strict standards that ensure legal admissibility. The report includes an executive summary for busy decision-makers, detailed methodology sections that explain exactly how evidence was collected and analyzed, and clear conclusions supported by the data. Every statement must be factual and objective—speculation has no place in forensic reporting.
Documenting findings requires meticulous attention to detail. Each piece of evidence gets precisely described, including its original location, how it was recovered, and why it’s significant to the case. Screenshots, data extracts, and technical diagrams help illustrate key points.
The biggest challenge is explaining technical concepts clearly without losing accuracy. Investigators must describe complex computer processes using everyday language that anyone can follow. Analogies and simple explanations help bridge the gap between technical reality and common understanding.
When cases go to trial, forensic analysts often provide expert witness testimony. This means explaining their findings under oath, defending their methods under cross-examination, and maintaining credibility while simplifying complex topics. The ability to communicate clearly becomes just as important as technical expertise.
Presenting evidence in a legal context requires understanding courtroom procedures and evidence rules. The chain of custody must be demonstrated, the scientific validity of methods must be established, and the reliability of tools and techniques must be proven. This legal framework ensures that digital evidence carries the same weight as physical evidence.
Computer Forensics vs. Cybersecurity: Clarifying the Connection
If you’ve ever wondered about the difference between computer forensic analysis and cybersecurity, you’re not alone. These two fields are often mentioned together, but they serve very different purposes in our digital world. Think of cybersecurity as your home security system – it’s actively working to keep intruders out with alarms, cameras, and locks. Computer forensic analysis, on the other hand, is like the detective who arrives after a break-in to piece together what happened and gather evidence.
The distinction is crucial for businesses trying to protect themselves. Cybersecurity takes a proactive approach, focusing on prevention and defense. It’s about building firewalls, monitoring networks, and training employees to spot phishing emails before they become problems. Computer forensics is reactive – it springs into action after an incident has already occurred, working to understand the scope of the damage and identify the culprits.
| Feature | Computer Forensics | Cybersecurity |
|---|---|---|
| Primary Focus | Reactive: Investigating incidents after they occur | Proactive: Preventing and defending against attacks |
| Goal | Identify, preserve, analyze evidence; reconstruct events; support legal action | Protect systems, networks, and data from threats; ensure continuity |
| Methodology | Meticulous evidence collection, analysis, reporting; chain of custody | Threat detection, vulnerability management, security architecture, incident response planning |
| Timeframe | Post-incident | Pre-incident and ongoing |
Here’s what makes this relationship so interesting: these fields don’t compete with each other – they complement each other beautifully. A strong cybersecurity program can significantly reduce the number of incidents that require forensic investigation. Meanwhile, findings from computer forensic analysis provide invaluable intelligence that helps cybersecurity teams strengthen their defenses against future attacks.
It’s like having both a good security system and a skilled detective on your team. The security system does its best to keep trouble away, but when something does slip through, the detective’s findings help you understand how it happened and how to prevent it next time.
What is DFIR (Digital Forensics and Incident Response)?
This is where things get really exciting – and where computer forensic analysis and cybersecurity truly join forces. Digital Forensics and Incident Response (DFIR) represents the best of both worlds, combining the investigative power of forensics with the rapid response capabilities of cybersecurity teams.
When a cyberattack hits your business, every second counts. Traditional approaches might force you to choose between stopping the attack quickly or preserving evidence for later investigation. DFIR eliminates that painful choice by doing both simultaneously.
DFIR teams work like emergency responders and detectives rolled into one. While part of the team focuses on containing the threat and minimizing damage, forensic experts are simultaneously collecting digital evidence from the active incident. This dual approach leads to faster remediation because the team understands the attack’s scope and methods in real-time, allowing them to more effectively eradicate the threat.
Evidence preservation during an attack becomes seamless rather than an afterthought. Critical volatile data from compromised systems, network traffic logs, and memory contents are captured before they disappear forever. This is especially important because much of this evidence would be lost if teams waited until after the incident was resolved.
The post-incident review phase is where DFIR really shines. Once the immediate threat is neutralized, the forensic evidence undergoes thorough analysis to reconstruct the entire incident timeline. This “lessons learned” approach helps organizations understand their vulnerabilities, improve their defenses, and build stronger protection against similar attacks in the future. Modern DFIR teams even incorporate proactive threat hunting, using forensic techniques to search for hidden threats before they cause damage.
At 1-800 Office Solutions, we understand that effective protection requires both strong preventive measures and skilled investigative capabilities when incidents occur. That’s why our comprehensive approach addresses every stage of digital security. For more info about our cybersecurity services, we’re here to help you build the right combination of proactive protection and responsive investigation capabilities for your business.
Real-World Applications and Why It Matters
The numbers tell a sobering story. The FBI reported a staggering 791,790 internet crimes in 2020 alone – a 69% spike from the previous year. Behind each statistic is a real victim: a small business owner whose customer data was stolen, a family dealing with identity theft, or a corporation facing millions in losses from a cyberattack.
This explosion in digital crime makes computer forensic analysis more than just a technical specialty – it’s become a critical defense mechanism for our increasingly connected world. When cybercriminals strike, forensic experts are the digital detectives who piece together what happened, how it happened, and who’s responsible.
The scope of these investigations spans everything from corporate boardrooms to criminal courtrooms. For detailed insights into how pervasive cybercrime has become, the 2021 FBI Internet Crime Report provides eye-opening statistics that underscore why digital forensics expertise is so crucial today.
Corporate and Internal Investigations
For businesses, computer forensic analysis often serves as both shield and sword – protecting valuable assets while uncovering internal threats that could destroy a company from within.
Intellectual property theft represents one of the most devastating corporate crimes. When a key employee suddenly leaves for a competitor, forensic analysis can reveal whether they took your customer database, trade secrets, or proprietary designs with them. Digital breadcrumbs – from USB insertions to email attachments – tell the complete story of what was accessed and when.
Employee misconduct investigations have become increasingly complex in our remote work era. Whether it’s harassment conducted through company messaging systems, fraudulent expense reports, or employees running side businesses on company time, digital evidence provides the objective truth that HR departments need to make fair decisions.
When data breaches strike, time is everything. Forensic experts work like digital crime scene investigators, determining exactly how attackers got in, what they accessed, and whether sensitive information was stolen. This analysis isn’t just about understanding the past – it’s essential for meeting regulatory reporting requirements and preventing future attacks.
Ransomware investigations have unfortunately become routine for many organizations. Beyond just recovering encrypted files, computer forensic analysis reveals the initial point of compromise, traces how the malware spread through networks, and identifies what data might have been stolen before encryption occurred.
Perhaps most challenging are insider threats – malicious activities by current or former employees who already have legitimate system access. These investigations require careful analysis of user behavior patterns, access logs, and data transfers to distinguish between normal work activities and suspicious actions.
Our comprehensive IT infrastructure services are designed to support these types of investigations when they become necessary. Learn more about how we help businesses maintain secure, auditable systems at More info about our IT services.
Criminal and Civil Litigation
The courtroom has become a battleground where digital evidence often determines the outcome. Computer forensic analysis provides the scientific rigor needed to make digital evidence stand up under legal scrutiny.
Law enforcement agencies now rely heavily on computer forensics for everything from fraud cases to homicide investigations. A suspect’s smartphone can reveal their location during a crime, deleted text messages can expose criminal conspiracies, and browser history can demonstrate intent. The famous BTK serial killer case was solved partly through metadata found on a floppy disk – a perfect example of how digital evidence can crack even the most challenging cases.
In criminal trials, forensic experts reconstruct digital timelines that can provide alibis or prove guilt. They recover deleted communications, analyze financial transactions, and trace online activities to build compelling cases that juries can understand.
Civil litigation increasingly depends on digital evidence too. Divorce proceedings often hinge on recovered text messages or social media activity. Employment disputes may be resolved through email evidence of discrimination or harassment. Contract violations can be proven through digital communications that show intent to breach agreements.
Electronic Findy (eFindy) has revolutionized civil litigation by requiring parties to produce relevant electronic information. Computer forensic analysis ensures this electronically stored information is properly identified, preserved, and reviewed – a process that can involve millions of documents and communications.
National and Corporate Security
At the highest levels, computer forensic analysis protects our most critical systems and sensitive information from sophisticated threats.
When cyberattacks target infrastructure like power grids or financial networks, forensic investigators work to identify the attackers, understand their methods, and assess the damage. This analysis is crucial for national security agencies determining whether attacks are criminal, terrorist, or state-sponsored in nature.
Corporate and industrial espionage cases require forensic experts who can detect subtle data exfiltration techniques. These investigations often involve analyzing network traffic patterns, identifying covert communication channels, and tracing intellectual property theft that may have occurred over months or years.
Government and corporate data protection relies on forensic capabilities to detect and respond to advanced persistent threats. When sensitive information is at stake – whether it’s classified government documents or proprietary business intelligence – computer forensic analysis provides the detailed investigation needed to understand security incidents fully.
Regulatory compliance frameworks like HIPAA for healthcare and Sarbanes-Oxley for financial reporting mandate robust incident response capabilities. When security incidents occur, organizations must demonstrate through forensic analysis that they’ve properly investigated the breach, understood its scope, and taken appropriate remedial action.
This intersection of technology, law, and security makes computer forensic analysis an essential capability for protecting both individual organizations and our broader digital infrastructure.
The Human Element: Roles, Skills, and Legal Boundaries
Behind every successful computer forensic analysis is a skilled professional who combines technical expertise with investigative instincts and unwavering ethical standards. It’s a field that’s exploding with opportunity – the Bureau of Labor Statistics job outlook shows information security analysts (which includes many forensic roles) will grow by an impressive 33% between 2020 and 2030. That’s much faster than average, creating thousands of new opportunities each year.
What makes this field so compelling is that it requires a unique blend of detective work and technical mastery. You’re not just analyzing data – you’re uncovering digital stories, piecing together evidence, and helping solve real-world problems that affect businesses and communities.
The skills needed go far beyond just knowing how to use forensic software. Technical proficiency in operating systems like Windows, Linux, and macOS is essential, along with understanding file systems and networking protocols. But equally important is analytical thinking – the ability to process massive amounts of data and spot the needle in the digital haystack.
Problem-solving skills are crucial because every investigation presents unique challenges. Maybe you need to bypass encryption, recover data from a damaged drive, or trace digital breadcrumbs across multiple devices. Attention to detail can make or break a case – missing a single timestamp or file fragment could mean the difference between solving a crime and letting a perpetrator walk free.
Perhaps most importantly, professionals in this field need strong communication skills. You might find the smoking gun, but if you can’t explain it clearly to a jury or corporate executive, your findings won’t have the impact they should.
Typical Job Roles and Responsibilities
The world of computer forensic analysis offers several career paths, each with its own focus and rewards. A Computer Forensics Analyst handles the full investigation process – from collecting evidence to writing the final report. These professionals often work for law enforcement agencies, government organizations, or private consulting firms.
Digital Forensics Investigators take on more of the detective role, interviewing witnesses and building comprehensive cases around digital evidence. They’re the ones who connect technical findings to real-world events and help tell the complete story of what happened.
Forensic Technicians focus on the hands-on collection and preservation of evidence. They’re the guardians of the chain of custody, making sure every piece of digital evidence is properly handled and documented from the moment it’s seized.
eFindy Specialists work primarily in the legal world, managing electronic findy for civil litigation. They help identify, preserve, and produce electronically stored information that’s relevant to legal cases.
Essential Skills and Qualifications
Getting started in computer forensic analysis typically requires a solid educational foundation – usually a bachelor’s degree in computer science, cybersecurity, or a related field. But the learning never stops in this rapidly evolving field.
Beyond the technical skills we mentioned, understanding legal procedures is absolutely critical. You need to know about search and seizure laws, rules of evidence, and courtroom protocols. Many professionals pursue additional legal training to complement their technical expertise.
Professional certifications can significantly boost your credentials and earning potential. The Certified Information Systems Security Professional (CISSP) demonstrates broad information security knowledge, while the Certified Cyber Forensics Professional (CCFP) focuses specifically on forensic skills. The GIAC Certified Forensic Analyst (GCFA) is highly respected for its hands-on approach to incident response and forensic analysis.
Legal and Ethical Boundaries in Computer Forensic Analysis
With great power comes great responsibility, and nowhere is this more true than in computer forensic analysis. The ability to peer into someone’s digital life comes with strict legal and ethical obligations that professionals must never compromise.
Fourth Amendment rights protect individuals from unreasonable searches and seizures, which means law enforcement typically needs a search warrant based on probable cause before examining digital devices. Forensic examiners must work strictly within the scope of that warrant – if they find evidence outside its boundaries, they must stop and obtain proper legal authorization.
The admissibility of evidence depends on maintaining strict protocols throughout the investigation. Every step must be documented, the chain of custody must be unbroken, and the scientific methods used must be reliable and accepted by the legal community.
Maintaining objectivity is perhaps the biggest ethical challenge. It’s tempting to develop theories about what happened, but forensic analysts must let the evidence speak for itself. Their job is to uncover facts, not to prove guilt or innocence.
Privacy concerns are increasingly important as our digital devices contain intimate details of our lives. Analysts must handle this information with extreme care, accessing only what’s relevant to the investigation and protecting privacy wherever possible.
The foundation of all forensic work rests on professional ethics – maintaining confidentiality, avoiding conflicts of interest, and always upholding the integrity of the forensic process. When these standards slip, vital evidence can be destroyed or rendered inadmissible, potentially undermining entire legal proceedings and allowing criminals to escape justice.
Conclusion
As our lives become increasingly intertwined with the digital world, computer forensic analysis has evolved from a niche specialty into an absolutely essential discipline. Think about it – every click, every file, every digital interaction leaves traces that can tell a story. When something goes wrong, whether it’s a data breach at your business or a criminal investigation, these digital breadcrumbs become the key to understanding what really happened.
The field bridges a fascinating gap between the highly technical world of computers and the very human need for truth and justice. From corporate boardrooms investigating employee misconduct to courtrooms where digital evidence can make or break a case, computer forensic analysis provides the scientific rigor needed to turn complex data into clear answers.
What makes this field particularly compelling is its incredible breadth of impact. We’ve seen how it protects national security by investigating cyberattacks on critical infrastructure, helps businesses recover from devastating ransomware attacks, and even solves murders where digital evidence provides the missing piece of the puzzle. The FBI’s statistics showing billions in annual losses from cybercrime underscore just how vital these investigative skills have become.
At 1-800 Office Solutions, we recognize that understanding digital risks isn’t just about having the right technology – it’s about having the right expertise when you need it most. Just as we help businesses streamline their operations with cutting-edge office technology and managed IT services, we understand that robust security measures and forensic capabilities work hand-in-hand to protect what matters most to your business.
The digital landscape will continue to evolve, bringing new challenges from cloud computing to IoT devices to technologies we haven’t even imagined yet. But the fundamental principle remains the same: when digital crimes occur, skilled professionals using scientific methods will be there to uncover the truth.
Whether you’re a small business owner wanting to protect your customer data or part of a larger organization managing complex IT infrastructure, staying informed about these capabilities and partnering with trusted experts makes all the difference.
Ready to take your digital security seriously? We’re here to help you build a comprehensive approach that protects your business from day one. Protect your business with our Computer Forensics Services and find how the right partnership can give you peace of mind in our increasingly connected world.