What is Penetration Testing: A Guide to Proactive Cybersecurity
Identifying and fixing security weaknesses before criminals exploit them is a fundamental business priority. Penetration testing provides a clear, actionable path to achieving this by simulating a real-world cyberattack against your systems. This guide explains what penetration testing is, how it works, and why it’s a critical investment for protecting your business assets, reputation, and bottom line.
Understanding the Core Purpose of Penetration Testing

At its heart, a penetration test answers a crucial question for every business leader: “How well would our defenses hold up against a determined attacker?” This simulated attack, often called a pen test, mimics the exact tactics and techniques real-world adversaries use to breach corporate networks.
Automated scanners can find common vulnerabilities, but they lack the creativity and persistence of a human hacker. A professional pen test fills that gap. Ethical hackers don’t just find flaws; they demonstrate their real-world impact. For example, a tester might chain together several seemingly minor issues to access sensitive customer data, revealing attack paths that automated tools would miss. This helps you prioritize fixes based on tangible business risk, not just a theoretical checklist.
Moving Beyond Simple Scans
It is important to distinguish penetration testing from vulnerability scanning. A vulnerability scan is an automated process that checks your systems against a database of known issues and produces a list of potential weaknesses. Think of it as a preliminary security check-up.
A pen test, however, is a deep, hands-on investigation. An ethical hacker takes the results from a scan and actively attempts to exploit the identified vulnerabilities. This manual effort confirms whether a flaw is a genuine threat and reveals the potential extent of the damage if a real attacker were to succeed.
A penetration test doesn’t just show you a list of unlocked doors; it walks through them to see what a burglar could actually steal, providing a true measure of your security posture.
The Business Value of Proactive Defense
The ultimate goal of penetration testing is to strengthen your entire security program. By identifying and remediating vulnerabilities in a controlled manner, you can prevent costly data breaches, avoid significant regulatory fines, and safeguard the reputation you’ve worked hard to build.
This proactive approach helps build trust with customers and partners. When integrated with a comprehensive understanding of cybersecurity in the modern office, regular testing transforms security from a reactive expense into a strategic investment that protects your organization’s long-term viability.
Exploring the Different Types of Penetration Tests
Penetration testing is not a one-size-fits-all service. The type of test your business needs depends on your specific digital assets and risk profile. Different tests simulate unique attack scenarios, targeting specific components of your IT infrastructure.
Understanding the various types of pen tests allows you to focus your security budget on the areas most critical to your operations. Choosing the right tests ensures you build a security strategy that effectively addresses your most significant threats.
Network Penetration Testing
This is a foundational form of testing focused on the security of your organization’s entire network infrastructure. Testers examine everything from servers and firewalls to routers and employee workstations to identify exploitable weaknesses that could lead to a breach.
Network tests are typically categorized into two types:
- External Network Testing: This simulates an attack from an outside threat with no prior access to your systems. The ethical hacker acts as a cybercriminal on the internet, probing public-facing assets like web servers and firewalls to find an entry point.
- Internal Network Testing: This test addresses the “what if” scenario of an attacker already inside your network. This could be due to a compromised employee account, a successful phishing attack, or a malicious insider. The objective is to determine how far an attacker can move laterally and what sensitive data they can access once past the initial perimeter.
Web Application Penetration Testing
Businesses rely heavily on web applications, from e-commerce platforms to internal management tools, making them a primary target for attackers. A web application pen test is specifically designed to uncover security flaws within an application’s code, configuration, and underlying logic.
Testers search for critical vulnerabilities such as SQL injection, cross-site scripting (XSS), and broken authentication. Securing these applications is essential for protecting customer data and maintaining business operations. For instance, an e-commerce site with an SQL injection flaw could allow an attacker to steal the entire customer database, leading to massive financial and reputational damage.
An application pen test goes beyond simple scans to find deep-seated coding and logic flaws that automated tools almost always miss. It’s the difference between checking if a door is unlocked and actually figuring out if the lock itself can be picked.
Cloud Security Penetration Testing
As organizations migrate infrastructure to cloud providers like AWS, Azure, and Google Cloud, new security challenges emerge. Cloud penetration testing focuses on identifying vulnerabilities specific to these environments, such as misconfigured storage buckets, insecure APIs, or overly permissive access controls.
Under the cloud’s shared responsibility model, the provider secures the underlying hardware, but you are responsible for securing what you build on it. A cloud pen test validates that your configurations are secure and meet industry best practices.
Social Engineering Testing
Attackers often find that the easiest way into a secure network is by targeting its people. Social engineering tests measure your team’s resilience to the psychological manipulation tactics used by cybercriminals.
These simulated attacks can take several forms:
- Phishing Campaigns: Crafting deceptive emails to trick employees into revealing credentials or downloading malware.
- Vishing (Voice Phishing): Using phone calls to impersonate IT support or other authority figures to extract sensitive information.
- Physical Pretexting: Attempting to gain physical access to facilities by posing as a delivery person, contractor, or new employee.
The insights from these tests provide valuable data for refining your security awareness training programs.
The amount of information a tester has beforehand also defines the approach. To learn more, see our guide on black box vs. white box pen testing. Understanding these methodologies helps you select a test that best simulates real-world threats to your organization.
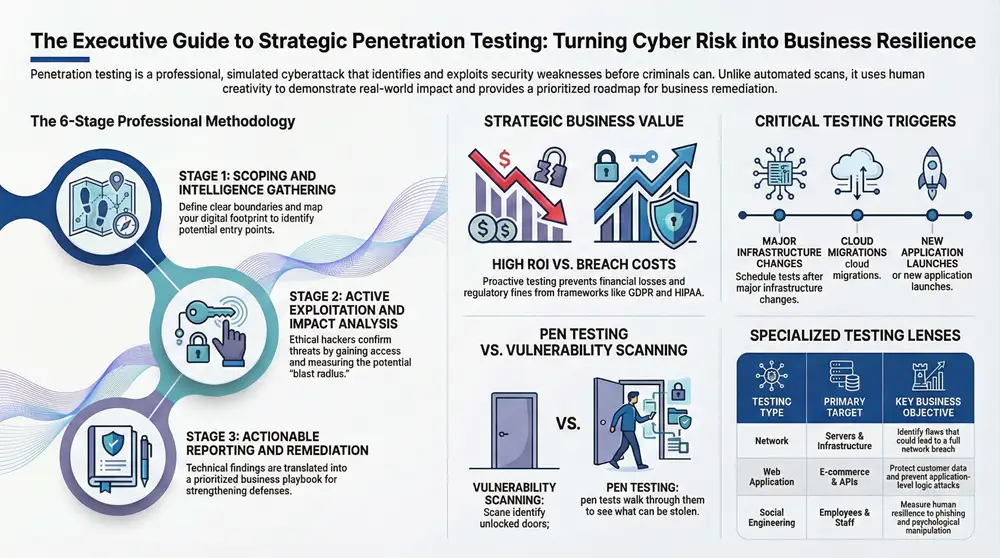
Penetration Test Types and Their Business Focus
| Testing Type | Primary Target | Key Business Objective |
|---|---|---|
| Network | Servers, firewalls, routers, workstations | Identify infrastructure weaknesses that could lead to a breach. |
| Web Application | Custom web apps, e-commerce sites, APIs | Protect customer data and prevent application-level attacks. |
| Cloud Security | Cloud configurations (AWS, Azure, GCP) | Ensure cloud environments are secure against misconfigurations. |
| Social Engineering | Employees, staff, contractors | Measure human vulnerability to phishing and manipulation. |
Each type of penetration test offers a unique perspective on your security posture. Combining them provides a comprehensive and realistic assessment of your organization’s defenses.
The Six Stages of a Professional Penetration Test

A professional penetration test is a highly methodical process designed to deliver clear, actionable results. It is not a chaotic attack but a strategic operation where each phase builds on the previous one, ensuring the assessment is both thorough and repeatable.
This structured methodology allows ethical hackers to accurately simulate real-world threats, systematically identify vulnerabilities, prove their exploitability, and measure the potential business impact of a breach. The final report serves as a comprehensive roadmap for strengthening your security.
This visual flow shows how different types of penetration tests target distinct areas of your business—from your network infrastructure and web applications all the way to your employees.
As the infographic suggests, a strong security strategy often needs a multi-pronged approach, combining different test types to cover all your bases. Now, let’s break down the six key stages that define a professional ethical hacking engagement.
Stage 1: Planning and Scoping
Before any testing begins, the most critical phase occurs: planning. The testing team collaborates with your organization to establish the rules of engagement. This involves defining goals, identifying target assets, and setting clear boundaries to ensure the test is both effective and safe.
Key activities include:
- Defining Objectives: Clarifying what constitutes success, such as gaining access to a specific database or testing a new application’s security.
- Establishing Scope: Determining which systems, networks, and applications are in scope and which are off-limits.
- Setting Timelines: Agreeing on a testing window to minimize disruption to daily operations.
Proper alignment in this stage prevents misunderstandings and ensures the test remains focused on your business’s most critical assets.
Stage 2: Reconnaissance and Intelligence Gathering
With the scope defined, the reconnaissance phase begins. The ethical hacker gathers as much information as possible about the target to map its digital footprint and identify potential entry points.
This can be done passively (using publicly available information) or actively (by directly probing systems). Intelligence gathered often includes IP addresses, domain details, employee information from social media, and the technology stacks used by your applications. This stage provides the raw material for the subsequent attack phases.
Stage 3: Scanning and Vulnerability Analysis
Armed with intelligence, testers proceed to the scanning phase. Using a combination of automated tools and manual techniques, they probe the in-scope systems for known vulnerabilities, open ports, and configuration errors.
However, a scan alone is insufficient. The crucial next step is vulnerability analysis, where a human expert analyzes the scan results to determine which findings are genuinely exploitable. This expertise is what distinguishes a true penetration test from a basic vulnerability scan; it filters out noise and prioritizes real, tangible threats.
Stage 4: Gaining Access and Exploitation
This is the phase most people associate with hacking. The ethical hacker actively attempts to exploit the identified vulnerabilities to gain unauthorized access to a system or application.
Exploitation is the critical proof-of-concept step in a penetration test. It moves a vulnerability from a theoretical risk on a report to a confirmed, practical threat that demands immediate attention.
This might involve using specialized software to breach an unpatched server, bypassing weak login credentials on a web application, or using credentials obtained from a simulated phishing attack. Successful exploitation confirms that a vulnerability poses a real and present danger.
Stage 5: Maintaining Access and Post-Exploitation
Gaining an initial foothold is often just the start. In the post-exploitation phase, the tester explores how far they can move from their initial entry point. This mimics an attacker’s actions as they attempt to escalate privileges, move laterally across the network, and locate sensitive data.
This stage is vital for understanding the true business impact of a breach. For instance, can a compromised web server be used to pivot to the internal finance database? This phase reveals the potential blast radius of a single, seemingly minor vulnerability.
Stage 6: Reporting and Remediation
Finally, all findings are compiled into a detailed report—the most valuable deliverable of the engagement. A high-quality report does not just list vulnerabilities; it explains them clearly within the context of business risk.
A comprehensive report should include:
- An executive summary outlining key risks in plain, non-technical language.
- Detailed technical findings for each vulnerability, including screenshots and evidence of exploitation.
- A risk score for each finding based on its potential impact and likelihood.
- Actionable, prioritized recommendations for remediation.
This document becomes your organization’s playbook for strengthening its defenses, transforming the insights from the simulated attack into concrete security improvements.
Why Regular Penetration Testing Is a Smart Investment
Penetration testing is more than a technical check-up; its real value lies in connecting technical findings to business outcomes like operational stability, customer trust, and financial health. It is a strategic investment in your company’s resilience and future success.
This proactive approach allows you to address vulnerabilities in a controlled setting, significantly reducing the likelihood of a real-world data breach—an event that can cause devastating financial losses, operational disruption, and legal challenges.
Protect Your Brand Reputation and Build Customer Trust
Your company’s reputation is one of its most valuable assets. A single security breach can shatter customer trust instantly. When customers entrust you with their data, they expect it to be protected. A public breach not only leaks data but also erodes confidence, often driving customers to competitors.
Regular penetration testing demonstrates a tangible commitment to security. It signals to customers, partners, and stakeholders that you are actively working to protect their information. In a market where security is a primary concern, this commitment can provide a significant competitive advantage.
By investing in penetration testing, you are not just securing data; you are securing the trust that forms the foundation of your customer relationships. This proactive stance is a priceless asset for long-term brand loyalty.
Meet Critical Compliance and Regulatory Requirements
Many industries are subject to stringent data protection regulations. Frameworks like PCI DSS (payment card data), HIPAA (healthcare), and GDPR (EU personal data) include specific security mandates. Non-compliance can result in substantial fines, reaching millions of dollars.
Penetration testing is often a required or highly recommended component of these frameworks. It provides independent, third-party validation that your security controls are effective. A clean pen test report serves as concrete evidence to auditors and regulators that you are meeting your compliance obligations.
Achieve a Strong Return on Investment
The growing demand for security validation is clear. According to Fortune Business Insights, the global penetration testing market was valued at USD 2.45 billion in 2024 and is projected to reach USD 6.25 billion by 2032. This growth is driven by the clear financial logic of proactive security.
When comparing the cost of a penetration test to the average cost of a data breach, the return on investment becomes evident. Identifying and fixing a single critical vulnerability can prevent an incident that would otherwise cost exponentially more in remediation, fines, and lost business.
Implementing frameworks like the ACSC Essential 8 is an excellent starting point for building a strong defensive baseline, and penetration testing is the ideal way to validate the effectiveness of those controls. Combined with regular vulnerability risk assessments, pen testing provides a complete and actionable view of your security posture.
Determining the Right Testing Frequency for Your Business
A common question from business leaders is, “How often do we need to do a penetration test?” The answer is that cybersecurity is a continuous process, not a one-time event. The ideal testing frequency depends on your industry, regulatory requirements, and the rate of technological change within your organization.
An annual test is a good starting point, but it is often insufficient for modern businesses. A single change—a new application launch, a cloud service migration, or a server configuration update—can introduce a critical vulnerability overnight. A static, yearly test can leave significant gaps in your defenses.
The right cadence integrates security testing into your business operations, shifting it from a reactive task to a continuous, strategic process.
Key Triggers for Scheduling a Penetration Test
A mature security strategy uses key business and technology events to trigger testing, ensuring assessments remain relevant and deliver maximum value. Knowing these triggers helps you stay ahead of emerging threats.
The most common scenarios that should prompt a penetration test include:
- Major Infrastructure Changes: Deploying new servers, migrating to a new cloud provider, or opening a new office introduces new variables and potential weaknesses that require validation.
- New Application Launches: Before deploying a new customer-facing web application or internal software, a pen test is essential to identify and fix vulnerabilities before they can be exploited.
- Regulatory Compliance Mandates: Regulations like PCI DSS (for handling credit card data) and HIPAA (for healthcare data) often require annual or recurring penetration tests to maintain compliance and avoid penalties.
- Post-Incident Assessment: Following a security breach, a pen test is non-negotiable. It is critical for verifying that the exploited vulnerabilities have been remediated and for identifying other weaknesses that may have been overlooked.
Establishing a Practical Testing Cadence
For most companies, a hybrid approach that combines regularly scheduled tests with on-demand assessments provides the best balance of compliance coverage and risk management. Industry data indicates a growing understanding of this need. For example, a recent industry summary found that about 32% of organizations conduct pen tests annually or bi-annually, with 51% wisely outsourcing this function to specialized firms. You can explore more emerging penetration testing statistics on Zerothreat.ai.
A penetration test is a snapshot in time. If your environment changes frequently, you need more frequent snapshots to get an accurate picture of your security posture.
A practical testing schedule might look like this:
- Annually: Conduct a comprehensive, network-wide penetration test to satisfy most compliance requirements and establish a solid security baseline.
- Quarterly: Perform smaller, targeted tests on your most critical, high-risk assets, such as your e-commerce platform or core financial systems.
- On-Demand: Initiate a test immediately following any of the key trigger events mentioned above to ensure new systems are secure from day one.
By basing your testing schedule on actual business risk, you ensure your security efforts remain aligned with your operations, protecting your organization as it evolves.
A Few Common Questions About Penetration Testing
To clarify these concepts, let’s address some of the most common questions business leaders and IT managers have about penetration testing. Understanding these practical details can help you make more confident and informed security decisions.
What Is the Difference Between a Penetration Test and a Vulnerability Scan?
These two terms are often confused, but they serve different functions. A vulnerability scan is an automated, high-level check. It uses software to quickly scan your systems and compare its findings against a database of known security issues, flagging potential weaknesses.
A penetration test, in contrast, is a deep, manual investigation conducted by a security expert. It begins where the scan ends. An ethical hacker attempts to exploit the potential weaknesses to confirm if they pose a real threat and demonstrate the potential impact of a successful attack.
A vulnerability scan tells you a door might be unlocked. A penetration test tries to open that door, walks inside, and reports back on exactly what a burglar could steal.
How Much Does Penetration Testing Cost?
There is no standard price for a penetration test; the cost depends on the project’s scope and complexity. A focused test on a single web application will be less expensive than a full-scale assessment of an entire corporate network.
Key factors that influence pricing include:
- The number of systems, applications, or IP addresses in scope.
- The complexity of the environment (e.g., cloud, on-premises, or hybrid).
- The type of test required (e.g., network, web application, social engineering).
While penetration testing is a significant investment, its cost is minimal compared to the financial and reputational damage of a data breach.
What Happens After a Penetration Test Is Completed?
The engagement does not end with the test itself. Afterward, you receive a detailed report that serves as a roadmap for improving your security posture. This document is the most valuable outcome of the process.
A professional report will always include:
- An executive summary that explains business risks in clear, non-technical language.
- Detailed technical findings for each vulnerability, including its severity and proof of exploitation.
- Actionable recommendations for remediation, prioritized by criticality.
A final, crucial step is often a re-test to verify that your team has successfully patched the identified security holes, confirming that your defenses have been strengthened.
Strengthening your defenses requires a partner who understands the entire security landscape, from proactive testing to rapid incident response. 1-800 Office Solutions offers comprehensive cybersecurity services, including professional penetration testing, to help businesses like yours find and fix critical vulnerabilities before attackers can exploit them. Our expertise ensures your security strategy is robust, compliant, and aligned with your business goals.
Secure Your Business with Expert Penetration Testing from 1-800 Office Solutions











