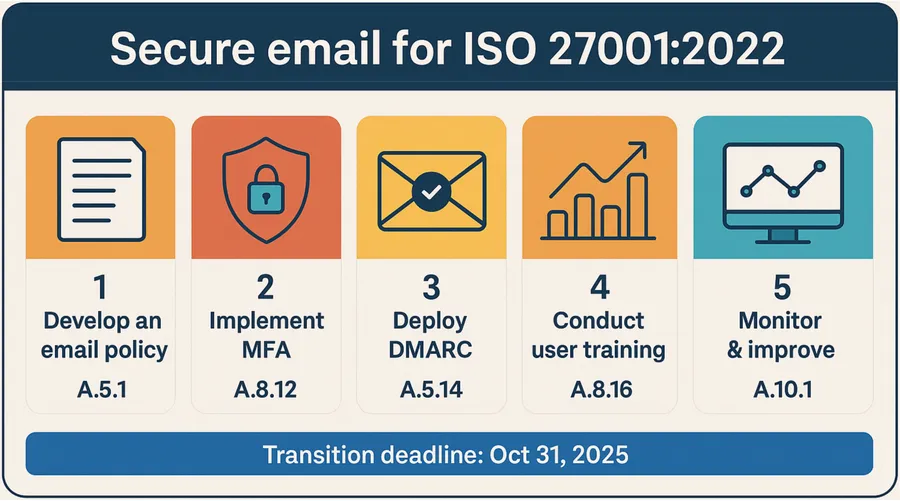
Why email security matters for ISO 27001
Email is still the easiest way into your systems—73 percent of incidentsstart with a phishing message. With ISO/IEC 27001:2022 certificates expiring on October 31, 2025, you need airtight email controls long before auditors arrive.This plain-English, five-step checklist shows you how to write a one-page policy, lock every inbox with MFA, authenticate your domain, block malware, and prove continuous monitoring—so you stay ahead of attackers and auditors.Ready? Let’s secure your inbox and keep your ISO journey on schedule.
Five practical steps to secure email for ISO 27001 compliance
Step 1: establish an email usage policy and continuous training program
Start by writing a one-page, plain-English email policy that spells out what staff may send, how to protect it, and what’s forbidden (auto-forwarding to personal Gmail, unencrypted attachments, and so on). Have every employee sign the policy and keep the acknowledgements on file—this alone checks ISO 27001:2022 controls A.5.1, A.5.14, and A.6.3, and puts you on the path toward ISO 27001 certification; control A.7 then covers staff onboarding and off-boarding.Next, reinforce the policy with ongoing awareness:
- Add confidentiality language to every contract and NDA. That extension to vendors maps to control A.5.34.
- Run phishing simulations every quarter and reward fast reporting. Human error still drives 75 % of cyber-attacks according to Trend Micro’s Annual Cybersecurity Report, so prompt, positive feedback matters more than shaming clicks.
- Keep the training drip-fed. Post a weekly “phish of the week” in Slack, drop a five-minute refresher into onboarding, and revisit the policy during all-hands. Consistency proves to auditors—and attackers—that security isn’t a one-off campaign.
Outcome: Everyone knows the rules, practices spotting real-world phish, and you have signed policies plus training logs to hand over when the auditor knocks.
Step 2: implement access controls and MFA for every mailbox
Locking down who can open, forward, or administer an inbox satisfies ISO 27001:2022 controls A.5.15, A.8.3, and A.8.4—and stops most breach attempts before they start.First, require a unique, long passphrase for every account. Use your password-manager policy to prevent reuse and turn off legacy POP/IMAP if they don’t support modern auth.Second, turn on multi-factor authentication (MFA) for all users. Microsoft reports that MFA blocks 99.9 % of automated attacks. Authenticator apps or FIDO2 keys work best; keep SMS only as a fallback. Record the MFA enforcement logs so you can hand them to an auditor.Third, apply least-privilege access:
- Grant admin rights only to the small team that needs them.
- Review shared mailboxes (support@, hr@) every quarter and document changes.
Finally, remove access the moment someone leaves. A same-day de-provisioning checklist should: revoke mailbox sign-in, strip admin roles, and clear any forwarding rules.Result: every active inbox is protected by a strong secret plus a second factor, no dormant accounts linger, and you hold clear evidence of access reviews—exactly what auditors look for, and exactly what attackers hate.
Step 3: secure your domain with SPF, DKIM, and DMARC
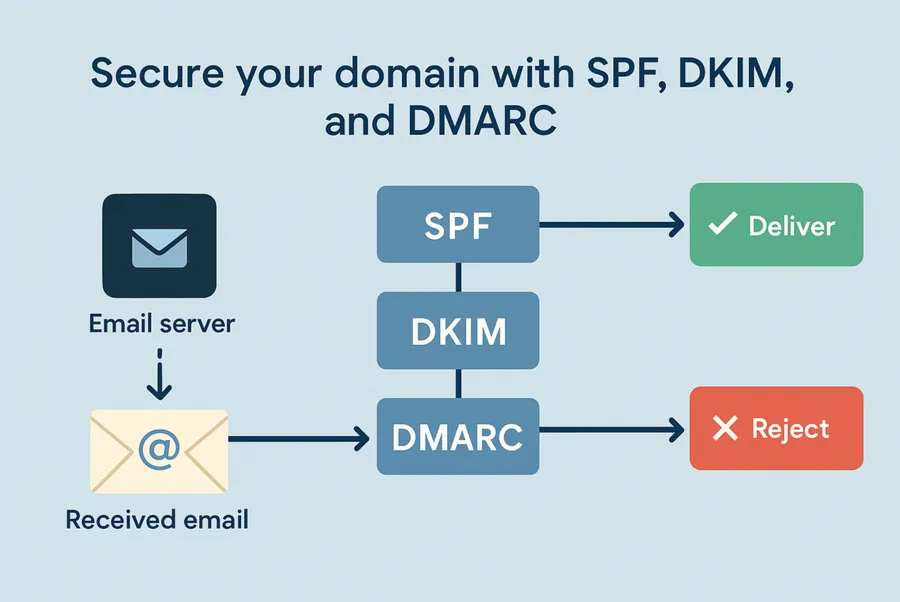 Publish three DNS records—SPF, DKIM, and DMARC—so recipients can prove your email is genuine. That single move satisfies ISO 27001:2022 controls A.5.14 (information transfer) and A.8.8 (technical vulnerabilities), and it keeps Gmail, Yahoo, and Microsoft from shunting your messages to junk after their 2025 policy changes.
Publish three DNS records—SPF, DKIM, and DMARC—so recipients can prove your email is genuine. That single move satisfies ISO 27001:2022 controls A.5.14 (information transfer) and A.8.8 (technical vulnerabilities), and it keeps Gmail, Yahoo, and Microsoft from shunting your messages to junk after their 2025 policy changes.
- List every legitimate sender in an SPF record. Add Microsoft 365, Google Workspace, your CRM, and any marketing tool, then confirm the record stays under the ten-lookup limit.
- Sign all outbound mail with DKIM. Turn on signing in your mail platform and publish the public key; rotate the key each year or whenever you change providers.
- Tell receivers what to do with failures by adding DMARC. Start with p=none to collect reports, tighten to p=quarantine, then move to p=reject once false positives drop to zero. DMARC adoption doubled in 2024 after Google and Yahoo made it mandatory, so auditors expect to see it.
- Review the DMARC aggregate reports each week. They highlight unknown senders and spot mis-configured services before attackers exploit them.
- Optional: add BIMI once DMARC is at reject. A verified logo in Gmail and Apple Mail boosts brand trust and shows you have your house in order.
Result: your domain can’t be spoofed without failing authentication, your marketing emails keep landing in the inbox, and you have clear evidence that ISO’s information-transfer controls are fully covered.
Step 4: block malware, filter spam, and encrypt every message
Attackers still send 94 % of malware through email attachments (Hoxhunt 2025), so ISO 27001:2022 demands technical defences under controls A.8.12 (malware), A.5.14 (information transfer), and A.8.21 (cryptography).Start by turning on advanced threat protection in Microsoft 365 or Google Workspace. Their real-time scanners open attachments in a sandbox and rewrite dangerous links before users click.Next, tighten the spam and phishing filters:
- Block known-bad domains and IPs pulled from threat-intel feeds (aligns with new control A.5.7).
- Quarantine first-time senders and anything that trips ML suspicion scores, then review daily.
To stop data from leaking out, apply data-loss-prevention rules that flag credit-card numbers, national IDs, or unencrypted spreadsheets leaving the company. If your mail provider lacks DLP, require sensitive files to be shared via a secure portal instead.Every message must travel encrypted, so require TLS for all SMTP connections and publish MTA-STS to prevent downgrade attacks. Add TLS-RPT so you can see if partners ever fall back to clear-text.Finally, keep a searchable archive. Cloud retention (Microsoft Purview, Google Vault) preserves a tamper-evident copy of every message—critical when auditors, lawyers, or incident responders need proof.Outcome: malicious payloads are stopped at the edge, sensitive data stays inside, and you can show auditors both the policy and the telemetry that prove these controls fire every day.
Step 5: monitor, respond, and improve continuously
Turn on unified audit logging today—Microsoft 365 and Google Workspace automatically record admin actions, sign-in failures, and forwarding-rule changes. Feed those logs into your SIEM, or into a GRC automation platform such as Vanta or another top GRC tool that continuously checks MFA status and user de-provisioning. Doing so meets ISO / IEC 27001:2022 controls A.8.16 (monitoring) and A.8.22 (event reporting).With visibility in place, write a one-page phishing incident playbook that answers four questions before the chaos starts:
- Who gets the first call (IT, security lead, legal)?
- How do you isolate a compromised device?
- When do you reset credentials?
- Which logs prove the scope of damage for SEC or GDPR disclosure?
Practice the playbook during quarterly tabletop drills; auditors love seeing the sign-in sheet from the last exercise.Every quarter, review your key metrics—phishing-simulation click rate, time-to-remediate, volume of quarantined mail, and inactive accounts removed. Use the numbers to decide whether to tweak DMARC policy, tighten spam thresholds, or refresh employee training. That loop closes ISO’s Clause 10 continuous-improvement requirement.Finally, subscribe to threat-intel advisories from CISA, NCSC, and your mail provider. New exploit kits that bypass MFA appear monthly; a two-minute read can prompt the next control you roll out.Outcome: you spot problems within minutes, respond with a rehearsed plan, and prove—with metrics and drill records—that email security keeps getting stronger rather than slipping out of date.
Wrapping up—stay compliant, stay secure
Email remains the easiest way in for attackers, which is why ISO 27001:2022 places such weight on communication controls. Follow the five actions you’ve just covered—write a policy, turn on MFA, authenticate your domain, block malware, and monitor continuously—and you’ll meet the standard while cutting real risk.Every control you’ve mapped today goes straight into the auditor’s checklist, and the transition deadline of 31 October 2025 leaves just enough time to embed them properly.Secure email means safer teams, smoother audits, and faster deals. Start ticking the boxes now.
Do we need DMARC to pass ISO 27001?
Yes—if you want a smooth audit and reliable deliverability. The standard doesn’t name DMARC outright, but it expects you to prevent spoofing under controls A.5.14 and A.8.8. Gmail, Yahoo, and Microsoft already junk unauthenticated mail, so auditors—and customers—treat DMARC at enforcement (p=quarantine or reject) as baseline hygiene.
What does ISO 27001:2022 require for email encryption?
Encrypt information in transit, every time. Control A.5.14 calls for secure transfer. Require TLS for all SMTP sessions, publish MTA-STS to block downgrade attacks, and use end-to-end or portal-based encryption for high-sensitivity data.
How often should we run phishing simulations and security training?
Quarterly phishing tests and continuous micro-training hit the sweet spot. ISO’s A.6.3 demands ongoing awareness, not a yearly fire-drill. Most teams run simulations every three months and drip quick tips in chat or newsletters each week.
Can we pass an ISO audit without an email-usage policy?
No—auditors will ask for it. Control A.5.1 requires a documented policy that staff have read and signed. Skipping it is the fastest way to earn a corrective action.
What counts as evidence of email controls?
Provide artefacts, not anecdotes:
Signed policy acknowledgements
• MFA and DMARC enforcement logs
• Phishing-test results and attendance sheets
• Screenshots of spam-filter settings
• User-access and de-provisioning records
If you can hand over those items on request, you’ll satisfy both ISO clauses and any curious stakeholder.