A Practical Guide to Cloud Computing Security Compliance
Achieving cloud computing security compliance is a non-negotiable requirement for modern businesses. This process involves adhering to specific industry and government standards like HIPAA, PCI DSS, and GDPR to protect data stored in the cloud. A robust compliance strategy not only secures sensitive information and prevents costly data breaches but also builds essential trust with customers, turning a regulatory necessity into a powerful competitive advantage.
Why Cloud Computing Security Compliance Matters
Migrating operations to the cloud offers significant advantages, but it also introduces complex security obligations. Ultimately, your organization is responsible for the data it manages in the cloud. Failing to meet compliance standards can lead to severe fines, legal challenges, and lasting damage to your business’s reputation.
However, strong cloud computing security compliance is more than a defensive measure; it is a strategic asset. It demonstrates to clients and partners that you are committed to protecting their data, a critical factor for business growth. Understanding the pros and cons of cloud computing is an excellent first step toward establishing a secure foundation.

This guide provides a clear roadmap for business leaders and IT professionals. We will cover:
- Key regulations and their specific requirements.
- The critical Shared Responsibility Model.
- Essential technical and administrative controls for implementation.
By the end of this guide, you will have a clear framework for transforming compliance from a complex challenge into a core operational strength.
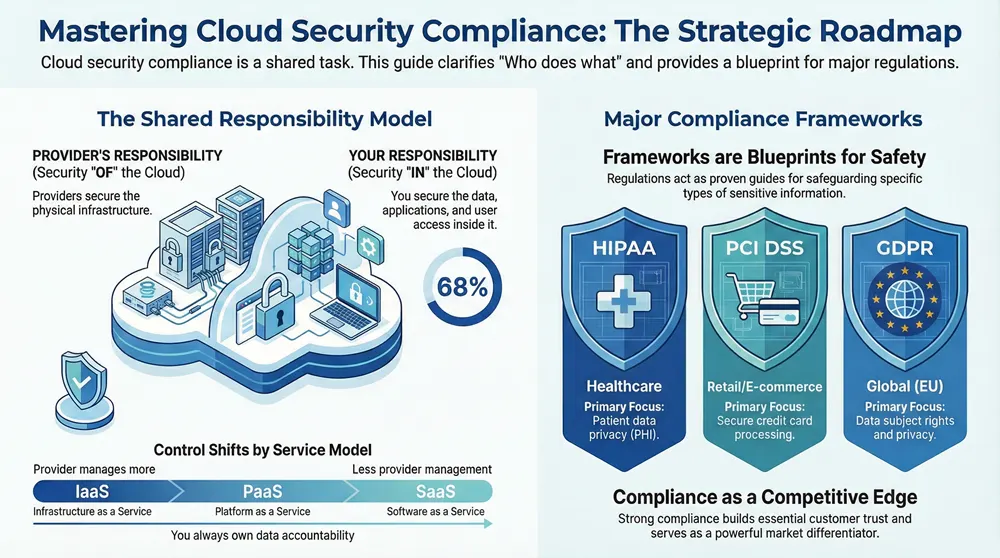
A core concept in cloud security is the Shared Responsibility Model. Misunderstanding this model is one of the quickest paths to creating significant security vulnerabilities. The model clearly defines which security tasks are handled by your cloud provider and which are your responsibility.
Imagine leasing a secure office building. The landlord (your Cloud Service Provider, or CSP) is responsible for the security of the building—the physical structure, perimeter security, and main entrance access.
As the tenant, you are responsible for security inside your office. This includes locking your suite, managing keycard access for your employees, and securing sensitive documents within your space.
Security OF the Cloud vs. Security IN the Cloud
This analogy highlights the model’s distinct division. Your cloud provider is always responsible for the security of the cloud, which includes the physical infrastructure that enables cloud services:
- Physical Security: Securing data centers, including buildings, guards, and surveillance.
- Hardware and Networking: Maintaining physical servers, storage, and core network infrastructure.
- Hypervisor: Managing the software that creates and runs virtual machines.
Conversely, your organization is always responsible for security in the cloud. This covers everything you build, store, or run on that infrastructure. You are accountable for:
- Data: Classifying, encrypting, and protecting your information.
- User Access: Implementing strong identity and access management (IAM).
- Client Endpoints: Securing devices that connect to your cloud environment.
The crucial takeaway is this: Your provider gives you secure building blocks, but you are responsible for using them correctly to build a secure application and protect your data. Assuming the provider is handling something that’s actually your job is a direct path to a breach.
How Responsibilities Shift Across Cloud Models
The line of responsibility shifts depending on the cloud service model you select—Infrastructure as a Service (IaaS), Platform as a Service (PaaS), or Software as a Service (SaaS). As you move from IaaS to SaaS, the provider assumes more responsibility, but you never delegate accountability for your data. You can learn more by reading about the three primary cloud computing models.
- IaaS (e.g., AWS EC2, Azure VMs): You have the most control and the most responsibility. You manage the operating system, middleware, runtime, data, and applications.
- PaaS (e.g., AWS Elastic Beanstalk, Google App Engine): The provider manages the OS and middleware, allowing you to focus on your applications and data.
- SaaS (e.g., Salesforce, Microsoft 35): You manage the least. The provider handles nearly everything, but you remain responsible for your data and user access configurations.
Understanding these distinctions is critical. Cloud misconfigurations remain a leading cause of security failures, accounting for 68% of all issues. This problem is escalating, as 83% of organizations experienced a cloud security breach in the last 18 months, often due to a lack of visibility into complex environments. You can dive deeper into these key cloud security metrics and findings.
Mastering cloud computing security compliance begins with understanding the regulations that apply to your business. These frameworks should be viewed not as obstacles but as proven blueprints for safeguarding sensitive data.
The array of compliance standards can seem complex, but they are categorized based on the type of information they protect, such as patient health records or customer credit card numbers. Identifying which regulations govern your operations is the essential first step.
Before exploring specific frameworks, it is vital to reinforce the shared responsibility model. While the cloud provider secures the underlying infrastructure, you are always responsible for what resides in the cloud—your data, applications, and user access. Adhering to this principle is non-negotiable for passing any compliance audit.
Major Cloud Compliance Frameworks at a Glance
This table outlines prominent compliance frameworks, their target industries, and the data they protect.
| Framework | Applicable Industry | Data Protected | Primary Focus |
|---|---|---|---|
| HIPAA | Healthcare & Associates | Protected Health Information (PHI) | Patient data privacy and security |
| PCI DSS | E-commerce, Retail | Cardholder Data (CHD) | Secure payment processing |
| SOC 2 | Service Organizations (SaaS) | Customer Data | Security, availability, and privacy controls |
| GDPR | Global (EU citizens) | Personal Data of EU residents | Data subject rights and privacy |
| FedRAMP | Government Contractors | Controlled Unclassified Information (CUI) | Security for U.S. federal agency data |
Each framework has unique requirements tailored to the risks associated with the data it protects. Let’s examine their practical implications.
HIPAA for Healthcare Organizations
For healthcare organizations, the Health Insurance Portability and Accountability Act (HIPAA) is the governing standard for handling Protected Health Information (PHI). This applies to providers, insurers, and any business associates who interact with patient data.
In cloud environments, HIPAA compliance centers on:
- Access Controls: Enforcing strict rules to ensure only authorized individuals can access electronic PHI.
- Encryption: Rendering PHI unreadable, both at-rest (on a server) and in-transit (across a network).
- Audit Trails: Maintaining detailed logs of who accessed PHI and their actions.
- Business Associate Agreements (BAAs): Formal contracts with your cloud provider that define their responsibilities for protecting PHI.
PCI DSS for Payment Card Data
Any business that accepts, processes, or stores credit card information must comply with the Payment Card Industry Data Security Standard (PCI DSS). Created by major card brands, its purpose is to prevent credit card fraud.
Key PCI DSS requirements include:
- Secure Network Configuration: Using firewalls to protect cardholder data.
- Data Protection: Encrypting card data during transmission and ensuring stored data is unreadable.
- Vulnerability Management: Regularly patching systems to defend against threats.
SOC 2 for Service Organizations
A SOC 2 (Service Organization Control 2) report is an independent audit that validates a service provider’s security controls. It assesses how a company manages customer data based on five Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy.
For SaaS companies and other businesses storing client data, a SOC 2 report is a critical tool for building customer trust.
A SOC 2 attestation is a powerful signal to the market. It tells potential customers that an independent third party has verified your security controls, which builds immediate trust and can be a significant competitive differentiator.
GDPR for European Union Citizen Data
The General Data Protection Regulation (GDPR) is an EU privacy law with global reach. If your business processes the personal data of anyone in the EU, you must comply. GDPR emphasizes transparency and individual rights. Practical tools like GDPR compliant HR software and Microsoft Purview integration show how these principles are applied.
Core GDPR principles include:
- Lawful Basis for Processing: Having a legitimate, documented reason for handling personal data.
- Data Subject Rights: Granting individuals the right to access, correct, and delete their data.
- Data Protection by Design: Integrating security and privacy measures into systems from the start.
FedRAMP for U.S. Government Agencies
The Federal Risk and Authorization Management Program (FedRAMP) is the standardized security assessment program for cloud providers working with the U.S. federal government.
Achieving FedRAMP authorization is a rigorous process based on NIST security standards. Often, having a solid security framework like ISO 27001 is a necessary starting point. In fact, many of the controls overlap; you can learn more about how email security plays a role in ISO 27001 compliance.
Implementing Essential Security Controls

Effective cloud computing security compliance relies on implementing robust security controls. These are the technical and administrative safeguards that form the backbone of your defense, transforming compliance theory into operational reality.
Without these foundational controls, any compliance plan is insufficient. This section details the essential safeguards needed to build a defensible security posture in the cloud.
Fortifying Access with IAM and MFA
The first line of defense is controlling who can access your systems and what they can do. This is the domain of Identity and Access Management (IAM). The guiding principle here is the principle of least privilege—grant users the minimum level of access required to perform their jobs.
This approach significantly reduces your attack surface. If an employee’s account is compromised, the potential damage is contained because their access is limited.
Multi-Factor Authentication (MFA) is no longer optional; it is a baseline for modern security. Requiring a second form of verification is proven to block over 99.9% of automated account compromise attacks.
Implementing MFA for all users, particularly administrators, is one of the most effective security measures you can take.
Protecting Data with Encryption
Once access is secured, you must protect the data itself. Encryption renders data unreadable to unauthorized users. For effective protection, you must encrypt data in two states:
- At-Rest: Data stored on servers, in databases, or in cloud storage.
- In-Transit: Data moving across networks, such as from a server to a user’s browser. Protocols like TLS (Transport Layer Security) protect data from interception.
Properly implementing both is a requirement for nearly every compliance framework.
Securing the Network Perimeter
A cloud environment still requires a secure perimeter. Cloud providers offer tools for creating isolated network zones. Virtual Private Clouds (VPCs) allow you to create a private section of the cloud, isolated from other tenants.
Within a VPC, security groups and network access control lists (ACLs) function as virtual firewalls. These tools allow you to define granular rules that control inbound and outbound traffic, preventing unauthorized network access.
Administrative Controls Human Safeguards
Technology alone is not sufficient. Your employees are a critical part of your security posture. Administrative controls are the policies and procedures that guide human behavior and promote secure operations.
Essential administrative controls include:
- Security Awareness Training: Regularly training employees to recognize phishing attempts, use strong passwords, and understand their role in protecting data.
- Incident Response Plan: A documented and practiced plan that outlines the exact steps to take during a security breach.
- Data Governance Policies: Clear rules defining how data is classified, stored, handled, and destroyed.
These controls are vital, as human error remains a significant factor in security incidents. Recent reports show that over 60% of organizations experienced a public cloud-related security incident in 2024, with a staggering 82% of all data breaches involving data stored in the cloud. Many of these issues, which cost businesses an average of $4.35 million per breach, stem from preventable mistakes like IAM misconfigurations. You can dig deeper into these cloud security statistics and their implications.
How to Prepare for Audits and Demonstrate Compliance
Achieving cloud computing security compliance is an ongoing process, but demonstrating it to an auditor is a distinct skill. A successful audit validates your security efforts, builds customer trust, and strengthens your market reputation.
The key is to adopt a culture of continuous compliance, where your organization operates as if every day is audit day. Your security posture should be consistently documented, monitored, and prepared for inspection. This approach transforms a stressful audit into a smooth validation of your existing security practices.
Systematically Gathering and Organizing Evidence
A successful audit depends on comprehensive evidence. Auditors require proof that your security controls are properly designed and functioning effectively. Your role is to create an organized library of documentation that aligns with each compliance requirement.
Key evidence includes:
- Policy and Procedure Documents: Official documentation such as information security policies, incident response plans, and data governance standards.
- Configuration Files: Snapshots of cloud service settings, firewall rules, and IAM policies.
- Access Logs and Reviews: Detailed logs showing who accessed sensitive data, along with records of regular access reviews.
- Vulnerability Scan Reports: Reports from regular scans that identify and track the remediation of vulnerabilities.
- Employee Training Records: Documentation proving that your team has been trained on security protocols.
Automating Compliance with CSPM Tools
Manually tracking configurations and permissions across a large cloud environment is impractical. Automation is essential. A Cloud Security Posture Management (CSPM) tool continuously monitors your cloud environment for deviations from your security baseline.
These tools are invaluable for audit preparation. They automatically detect misconfigurations, such as publicly accessible storage buckets or overly permissive IAM roles, and provide real-time alerts.
One of the biggest wins with a CSPM is its ability to generate audit-ready reports with a click. Forget spending weeks digging through logs. You can instantly produce detailed documentation showing your compliance over time, complete with a full paper trail of how you fixed any issues that popped up.
This level of automation saves significant time and provides a level of accuracy unattainable through manual checks.
During an audit, preparedness and transparency are crucial. The process typically includes interviews, document reviews, and system walkthroughs. Designate a single point of contact to ensure auditors receive consistent and accurate information.
Auditors are there to verify compliance, not to find fault. Treat them as partners. Be prepared to explain your controls, demonstrate them in action, and provide the organized evidence you have gathered.
If a gap is identified, view it as an opportunity for improvement. Understand the issue and present a clear remediation plan. This proactive approach demonstrates maturity and a commitment to security.
Your Action Plan for Sustainable Cloud Compliance
Maintaining cloud computing security compliance is a continuous cycle of assessment, improvement, and vigilance. This ongoing commitment protects your data, builds customer trust, and strengthens your business.
When sustained, compliance becomes an integrated discipline rather than a recurring task. A successful strategy requires a clear, actionable plan that embeds security into your company culture. A key component of this is mastering cloud governance, which establishes the foundational rules for securing your cloud resources.
Your Essential Compliance Checklist
To maintain momentum and ensure comprehensive coverage, focus on these four critical areas. This checklist serves as a repeatable plan for long-term success.
- Clarify Your Responsibilities: Regularly review the Shared Responsibility Model with your cloud provider. Document precisely which security tasks your team is responsible for versus what the provider handles, especially when adding new services.
- Identify and Monitor Regulations: Stay informed about the compliance standards that apply to your business, such as HIPAA, PCI DSS, or GDPR, and monitor for any updates.
- Implement and Validate Controls: Regularly audit your Identity and Access Management (IAM) policies, verify encryption protocols, and test your incident response plan. These checks ensure your defenses remain effective against evolving threats.
- Maintain Audit Readiness: Operate as if every day is audit day. Use automated tools like CSPM to continuously monitor your environment. Maintain an organized and accessible library of evidence, including logs, reports, and policy documents.
The real goal here is to build a security culture. When you do that, compliance becomes the natural result of smart processes, not something you scramble to fix. This proactive mindset slashes your risk and turns the stress of an audit into a simple exercise of showing off your strong security posture.
The path to sustained cloud compliance can be challenging. If the technical details and evolving regulations feel overwhelming, consider partnering with a managed security service provider.
An expert partner provides specialized knowledge, advanced tools, and dedicated oversight to keep your cloud environment secure and compliant. This allows your team to focus on core business objectives, confident that your security is in capable hands.
Common Questions About Cloud Compliance
Even with a solid plan, questions about cloud computing security compliance are common. The details can be complex, and the consequences of non-compliance are significant. Here are answers to some frequently asked questions.
What Is the Biggest Mistake Companies Make in Cloud Compliance?
The most common and costly mistake is assuming the Cloud Service Provider (CSP) is solely responsible for security and compliance. This misunderstanding of the Shared Responsibility Model creates critical security gaps, particularly in data protection, access management, and application security.
While the CSP secures the cloud infrastructure, the customer is always responsible for securing their data and workloads running in the cloud. A simple misconfiguration of a security setting or user permission can lead to a major data breach and compliance failure, regardless of the cloud platform.
How Does Multi-Cloud Affect Security Compliance?
A multi-cloud strategy complicates compliance efforts. Each CSP has unique tools and security features, making it difficult to enforce consistent policies across all environments. This fragmentation increases the risk of misconfigurations and security blind spots.
To manage this complexity, centralized security tools are essential. Solutions like a Cloud Native Application Protection Platform (CNAPP) or Cloud Security Posture Management (CSPM) provide a unified view and consistent policy enforcement across different clouds. Without a centralized approach, demonstrating compliance becomes significantly more difficult.
The bottom line is that a fragmented security approach in a multi-cloud world is unsustainable. Unified visibility is not a luxury; it is a core requirement for maintaining control and demonstrating compliance across diverse cloud platforms.
Is My Business Compliant If Our Cloud Provider Is Certified?
No. A cloud provider’s certification does not automatically make your business compliant. Their certifications (e.g., for HIPAA or PCI DSS) cover their responsibilities under the Shared Responsibility Model—their infrastructure and services.
Your organization remains fully responsible for how you configure and use those services to store, handle, and transmit sensitive data. For example, even if your CSP is HIPAA compliant, you are in violation if you misconfigure a cloud storage bucket containing patient records and make it public. You must build your own compliant architecture and processes on top of the provider’s certified foundation.
Staying on top of cloud computing security compliance demands real expertise and constant watchfulness. At 1-800 Office Solutions, we offer comprehensive managed cybersecurity services designed to help your business achieve and maintain compliance, protecting both your data and your reputation. See how our experts can fortify your cloud environment by visiting us at https://1800officesolutions.com.











